The Onion Router. Escaping the prying eyes of Control Society

http://www.experto.de/anonym-surfen-708px-600px.jpg
Last week, first of October, the FBI arrested Ross Ulbricht who is the alleged operator of the digital drug network known as the Silk Road. The Silk Road is a website which is accessible through The Onion Router (TOR) network. TOR network allows for internet users to encrypt their traffic data and remain anonymous. Internet users from censored countries use this network to remain anonymous, whistle-blowers use it to stay untraceable and drug dealers use it to deal drugs with use of bitcoins.
Until recently it was believed that TOR network provided an uncrackable anonymous and encrypted network service. However, as the leaks of the whistle-blower Snowden shows, the NSA has found a way to “hack” TOR network. The media attention toward TOR network calls for a critical analysis of this network. In the light of the NSA scandal privacy concerns come to surface of everyday debates. Here we want to uncover the technical implications of TOR and relate it to Deleuze’s concept of the control society.
What is TOR
On their website they describe the service as following:
Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.
So how does this work? As Galloway and Thacker point out internet protocols consist out of four layers: the applications layer, transport layer, internet layer and the link layer. ((Galloway Alexander R. and Eugene Thacker, ‘Protocol, Control and Networks,’ Grey Room 17 (2004): 14)) The application layer is responsible for the content which is being trafficked. It is at this layer where The onion routers most important function resides. ((Goldschlag, David M, Michael G. Reed and Paul F. Syverson, “Hiding routing information”. Workshop on information hiding. Cambridge, UK (1996): 4))



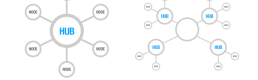
To simply summarize the visuals above, the traffic from point A to B is being encrypted. TOR clients encrypt the data by hiding packages into packages, this is why there is a reference to a onion since an onion has multiple layers. Whenever a client connects to a server, a random path is taken. This way the user remains anonymous.
TOR and Control Society
In Deleuzes short essay postscript on the societies of control he describes a model of society that moves beyond the disciplinary society of Foucault. A society where its people no longer move between vast spaces of enclosure, instead they appear to be ”free” to go where they please. However, within this freedom they are perfectly controlled.
A control is not a discipline. In making freeways, for example, you don’t enclose people but instead multiply the means of control. I am not saying that this is the freeway’s exclusive purpose, but that people can drive infinitely and “freely” without being at all confined yet while still being perfectly controlled. This is our future. ((Deleuze cited in Galloway Alexander R. and Eugene Thacker, ‘Protocol, Control and Networks,’ Grey Room 17 (2004): 11))
This example of the freeway perfectly fits the internet as we know it today. It is no coincidence that the topology of the internet fits that of Eisenhowers highway system in the U.S. Both are distributed networks where people can travel freely to any point, even when a node is down. However, and this becomes more clear in the case of the internet, control is everywhere. The leaks by Snowden show how the NSA is tracking internet traffic all over the world. However, according to Deleuze, it is the corporation which is the one who is controlling. “…in a society of control, the corporation has replaced the factory, and the corporation is a spirit, a gas.” ((Deleuze, Gilles. ‘Postscript on societies of control,’ October 59 (1992): 4 )) Later he mentions that “[w]e are taught that corporations have a soul, which is the most terrifying news in the world.” ((Deleuze, Gilles. ‘Postscript on societies of control,’ October 59 (1992): 76)) We all know that it is not just the NSA who is tracking us. Facebook, Google, Amazon, etc. constantly analyse our browsing behavior in order to sell better advertisements.
So how does TOR network fits into this story? Deleuze points out that “[t]here is no need to fear or hope, but only to look for new weapons” ((Deleuze, Gilles. ‘Postscript on societies of control,’ October 59 (1992): 4 )). Galloway and Thacker mention a “counter-protocol” and explain that “[t]he goal is not to destroy technology…but to push technology into a hypertrophic state, further than it is meant to go” ((Galloway Alexander R. and Eugene Thacker, ‘Protocol, Control and Networks,’ Grey Room 17 (2004): 25)) With TOR the user is using the distributed nature of the network to its limits, further than it is meant to go, by taking random paths and encrypted packages we are still following the rules of the internet protocols. However, by using TOR we escape from the prying eyes of the society of control. Except we are still using the same network, the same infrastructure and the same “freeway”. You use it in an anonymous fashion, but that is like driving on the freeway without a license plate. So we would like to leave you with a final question. By using systems like TOR, do we truly escape the control society?
Footnotes