Lessons in anti-security: tactical media and viral art
The following report is the outcome of two three hour sessions held in the context of the New Media course “Critical Media Art”, exploring the ideas and practices of ‘tactical media‘, in particular the use of viral tactics by artists, programmers, activists, and their collaborations. In the first session, media theorist Erik Kluitenberg gave a lecture on the history (and possible futures) of tactical media, especially its current application in the recent Arab Spring and Occupy social movements (see: Legacies of Tactical Media – The Tactics of Occupation: From Tompkins Square to Tahrir). In the second session, we discussed the role of the virus in media art and activism, asking the students to design a virus, and explain how it could be tactically and critically employed.
1. Curatorial Statement
The re-appropriation of vernacular and popular manners of speech to simplify and delineate technical terms of the current Information Age have been a persistent trend to describe a continual increase of technical workings of the online realm. The process of re-appropriation is often a residual process, based on characteristics of earlier compelling events, which bare enough significance to a new online phenomenon to help the common man envision its workings in a more mundane way. The 1980s, which saw the spread of AIDS (and the conspiracy theories concerning its origin), is an example of how these affections became interpreted as cultural objects across a variety of media platforms, to contextualize, analyze and experiment with, the unique logic of contemporary networks. Strikingly, whereas terms such as “cookies,” “firewall,” “surfing,” and “window” are rather obfuscating metaphoric descriptions, the way a “virus” is described originally in biology to a large extent overlaps with its actual evolution and function in computer networks. Besides computer viruses (self-replicating bits of code), there are such things as ‘viral marketing‘, viral videos, spam, botnets, and so on (sometimes called ‘memes’).
Already in the 1970s, Deleuze and others saw the rise (and potential appropriation) of viral-like dynamics, and celebrated a viral or rhizomatic subjectivity (and praxis) vis-a-vis the rigid and disciplined subjectivities of industrial societies. Sabotage and infection were seen as one of few modes of resistance left in the society of control (see Jussi Parrika). But the celebration of these kind of new subject formations was later criticized when it became apparent that many of the tactics of the emancipatory movements of the sixties and seventies were increasingly adopted by what is sometimes called ‘communicative capitalism‘. This co-incidence was for example described by Negri and Hardt in Empire: capitalism was redescribed (ironically in terms put forward by Deleuze and Guattari) as a parasitic apparatus of capture, i.e. behaving like a virus/vampire devouring its host (the laboring and socialized multitude). Indeed, having found its adequate objective means in the World Wide Web, viral strategies are increasingly adopted for ‘branding‘ purposes, via spam, or via users massively sharing content (a form of crowdsourcing). On the other hand, the democratization of means of (media) production simultaneously provided this very multitude with the same tools (e.g. to create viruses). Tactical media – as theory and practice – is a response to precisely this complex whole. It reacts, practically and theoretically, to a felt inadequacy of more traditional modes of resistance and analysis, respectively.
This ‘complex whole’ resists any clear cut distinction between strategy and tactic, as originally proposed by Michel de Certeau and partly foundational of the tactical media project. Far from implying the redundancy of using media tactically, new forms of interaction and communication are opened up by this ‘levelling of the playing field’ in recent years. The reifying strategies of yesterday’s overlords have been revolutionized to such an extent as be qualitatively transformed in a highly dynamic complex of ‘glocal’ microtactics. But this means that they are also increasingly ‘sensitive’ to tactical interventions (like viruses). The detranscendentalization of sovereignty opens up a new ‘space of communicability’ between formerly fragmented spheres (something terrorists have known for a while). A flash mob might not durably transform the existing stratifications of a given social space: but a virus can structurally harm infrastructures highly dependent on computation, information and communication (as governments and militaries are also discovering). Whereas the flash mob is often ‘lost’, the virus is perfectly at home in today’s networks. The distinction between host and virus is disappearing. Hence the idea of Occupy as a virus of a virus.
The virus is perceived by many as a security threat, a purposeful harmful anomaly that threatens the metastability of any given network. Apparently, the idee fixe of self-organization is mistrusted even by the neoconservative, managerial elite that it itself employed so successfully against the perceived threats of ‘big government’). If contemporary networks tend to become increasingly barricaded castles (or better: supervised highways), fueled by fears of contagion by biological or computer viruses, there arises a new sense of the strategic, not as a hegemonic space, but as a counter-tactics: to correct the multiplications of feedback to proportions high enough to prevent a fatal inertia (as in the recent financial crises), but low enough not to crash the whole system (see: Jaromil, below) and accomodate ‘suspect elements’ (hackers, terrorists, etc.).
Like most tactical media, the tactically employed virus evaporates when it has caused the aimed disruption to avoid a political trajectory and thereby consciously chasing a political agenda. It aims solely to disrupt, awaken, and raise awareness, but leaves the actual execution, the affirmative action to others.
The viral logics increasingly used by artists points to the importance of the historically unique agency of the object. In terms of activism: the subversive, political, revolutionary, resistant subject can delegate and automate his “acting potential” to digital objects, like viruses. The virus can ‘protest’ in-place of the human protester. It can behave tactically, in-place of the subject. And potentially more effectively so, since its protocol is that of its environment, the Internet. In the future, we will perhaps witness more hybrid formations of viruses and humans together reaching a certain threshold or critical mass of production that is able to have a real impact. This is a typically artistic or aesthetic procedure. If theory proceeds by grasping the crises of financial and housing markets by applying to it the heavy categories of relations and forces of production, the geek artist-activist experiments with the language of these processes themselves, actively manipulating them. The mode of its understanding is performative, a practical mimesis: “an artistic statement about computer viruses can only be expressed effectively by spreading a virus itself.” Since these processes are so far beyond representation as to elude capture in traditional theoretical or artistic critiques, artists paradoxically have to step beyond and even against representation, and engage in the design of a rather abstract and linguistic object-agency. For this, interdisciplinary ‘intelligent assemblages’ (e.g. programmers) is crucial.Vice versa, the programmer is invited to reflect on his own practices, and perhaps politicize him or herself, beyond the instrumental blindness typical of most technical labor. Viral art is one of the sites in which this paradoxical project of tactical media art is executed in collaboration with computer scientists, hackers, and political activists, of which some examples will now be discussed.
2. Five Viral Art Projects
I – Biennale.py
0100101110101101.ORG and EpidemiC / http://www.0100101110101101.org/home/biennale_py/
Hacker collective EpidemiC and artist duo 0100101110101101.ORG created a virus called ‘Biennale.py’ for the 49th Venice Biennale in 2001. An infected computer was displayed, on which files written in Python were corrupted untill the whole thing crashed. But the virus quickly left behind the white cube, and is to this day listed by the big antivirus companies. The source code was also distributed physically, setting of a virus there, carried on T-shirts (of which 1500 were sold). In turn, the media went bananas over the art project, creating another virus, fueled by the security expert’s form of ‘morality’:
“If a thief leaves a note saying he’s sorry, do we feel better? No,” said Jason Catlett, the president of an anti-spam group called Junkbusters, who has testified before Congress on Internet privacy issues. “Doing things that are socially undesirable in the name of art does not redeem the act.”

II – Forkbomb
Jaromil / http://jaromil.dyne.org/journal/forkbomb_art.html
Source Code:
:(){ :|:& };:
This little UNIX program (called a ‘forkbomb’) launches two copies of itself at startup which sets off a chain reaction with an exponentially growing number of processes, that eat up all the computer memory and CPU time, effectively crashing the computer. The program consists of only twelve characters. Jaromil explains the inherent relation between coding and aesthetics, the corresponding politics involved on this intersection, as well as placing his work in a specifically artistic tradition:
“In considering a source code as literature, I am depicting viruses as poésie maudite, giambi against those selling the Net as a safe area for a bourgeois society. The relations, forces and laws governing the digital domain differ from those in the natural. The digital domain produces a form of chaos—sometimes uncomfortable because unusual, although fertile—to surf thru: in that chaos viruses are spontaneous compositions, lyrical in causing imperfections in machines made to serve and in representing the rebellion of our digital serfs.”
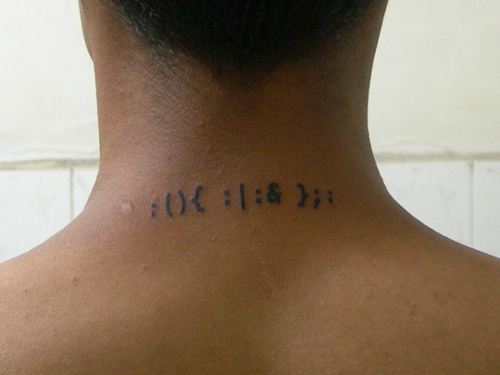
III – Vi-Con
Luca Bertini / http://www.vi-con.net/
The artist created two viruses (Yazna and ++) that search for each other on the net. One or the other infiltrates a computer, leaving a temporary signature that does not damage the host, which the other virus – if it hits that computer – recognizes. A love play between two viruses that treats the host contingently, as the indifferent condition of another community.
IV – DOGS
Sintron / http://www.runme.org/project/+dogs/
False virus notifications (or virus hoaxes) spread via email are not very different than actual viruses, in terms of how they proliferate as information. They are also often used in combination with actual computer viruses that lure the user into opening the file. The most famous virus hoax ever is an email warning for another email presumably containing a “Goodtimes” virus as an attachment. The email warning for the virus itself spread like a virus, scaring millions of people.
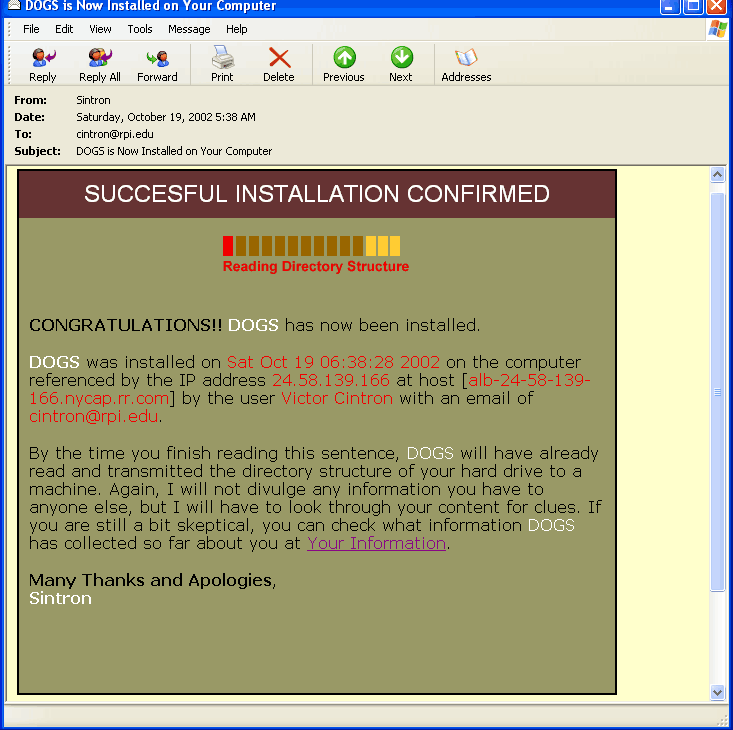
DOGS is a surveillance simulation application. Sintron explains:
“It sent an email message originating from Sintron’s email address, to a pre-selected address list which informed them that he had found out that an embarrassing secret of his was being spread about and that he would find out who discovered his secret by installing a spyware application on everyone’s machine in order to read their emails and hard drives for information. Whoever opened the initial email and had the proper email reader automatically sent a message back to DOGS which then immediately sent the “DOGS is Now Installed on Your Computer” email. That email contained a congratulatory remark, an animated gif of a progress bar that blinked a “Reading Directory Structure” message, the recipients name, IP address and email address, and a link that when opened, simulated the display of the contents of their hard drive on the web.”
V – Bocconi Virus
EpidemiC / http://epidemic.ws/bocconi/index.html
“As a classic form of “worm” based on the Microsoft Outlook© service, ‘bocconi.vbs’ sends itself, as an attachment, to every e-mail address available on the guest system, inviting the user to visit www.uni-bocconi.it. ‘bocconi.vbs’ creates a textual document (bocconi.txt) in the startup directory, and a print in ASCII characters of the Bocconi logo will be appear on the monitor at every startup of Windows©.”
Epidemic places itself in an artistic tradition, as opposed to what they call ‘collectable art’, the latter being based on mechanisms of ‘privation’ (or: ‘aura’). They also point to the possibilities of art in network culture, and the need to go beyond art’s (self)imposed limits, the need to recognize, and experiment with, “the abnormal possibilities of computer viruses” that have untill now, according to EpidemiC, “been impeded by conceptual and ideological barriers”.

For more examples of software and viral art, see http://www.runme.org
3. Workshop: Design your own virus
Students were invited to develop a concept for a virus or viral object of some kind that uses a Tactical Media approach in order to achieve a certain (political or social) goal. The assignment required students to critically consider the following questions:
– What kind of tactical media characteristics would your virus or viral object have?
– What would it look like? (make some kind of symbol or logo)
– What would it do? (what would it say / do with you screen)
– Would it be destructive or friendly?
– Would it be politically motivated/activist/raising awareness; what goal would it have?
Results
I – The End of the World, Dawg
The “End of the World”-virus is a virus that causes a complete computer shutdown on the Mayan Doomsday of the 21st of December 2012. On this day each ‘victim’ is forced to live an offline live without the comfort of a personal computer. On December 22nd, computers will restart and the following question will pop up: “Was this really the end of the world? O Yes, O No”. When people click “No” their computer will function normally again. When people click “Yes”, however, their computers will remain unusable indefinitely. The idea behind the virus is that, hopefully, word will get out that people will have to tick the “No”-option, thereby admitting that live without computers is not the end of the world.

II – Dec0yDIYDOI.5irus
In response to the current ACTA and SOPA threats to freedom of information on the internet, this virus is an anticipation to a future where ‘bots’ of organizations fighting copyright infringement scan the Digital Object Identifier (DOI) of data on personal computers to find illegal copies of copyrighted material. The virus, called Decoy-DIYDOI, detects these bots and intervenes in the process by making copies of illegal files and attaching a different DOI to them. In a ball-in-cup-fashion, some of these copies are dummy-files, some of them the real thing, making it impossible for these bots to effectively hunt down illegal content.

III – Long_livE_el/g00G
Although Google’s informal slogan is “Don’t be evil”, the company has often been accused of violating the privacy of its users. To create awareness that, by the combination of the data collected through its search engine, email service, browser and Google+ social network, Google might know a lot of private information about you, this virus will hack your login information to display highly ‘confidential’ and personal search results and advertisements based on the information available to Google. By displaying this personal information the virus is used to spark debate about the violation of privacy by Google and to raise awareness on Google’s practises.

IV – SPhinxXX
In light of Nicolas Carr’s argument that Google might be “making us stupid”, this group quiet radically pose the possibility of creating a Facebook app-virus that blocks internet access to those deemed “not intellectual enough”. When infected, the user will have to answer an intellectual question before being able to access the internet. When the answer is correct, the user ‘earns’ one day of internet (i.e. the internet connection functions normally). When the question is not answered correctly, no internet connection will be possible, ideally forcing the user to look up the answer to the question the ‘traditional’, intellectual way by visiting libraries, talking to experts etc. By blocking internet access, the virus is used to force people to return to more conventional—and in this group’s view better—ways of acquiring information.

[Stay Alert, folks. The virus is always nearer than you imagine it to be (you silly, clumsy mammal!)]
This post was presented to you by: Leander Roet, Jeroen Rijskamp and Daniel de Zeeuw.
Workshop images: All Rights Reserved, © 2012, Michael D.’s iPhone.