Breaking the illusion of Control: “Home -1.0”
-
Introduction: Idea and Aim of the Project
A recent innovation towards ultimate control is Apple’s “Home” app, which can command all smart devices in a house, from lamps to locks. But who gains power with this app? Is it really the user? But he already controls his home manually. Or is it more Apple because it receives tons of information on the users’ habits? Although many people have heard of the internet of things and smart home devices, they do not seem to be aware of what happens with their data when they use these things – in this case, through “Home.” If you google the terms “Apple, Home, app, privacy”, there are only a few results dealing with privacy issues of “Home.”
Therefore, we created this blog called “Home -1.0.” It is called “-1.0” because it resembles a deconstructed version of the app, showing what happens underneath from Apple’s point of view – the hidden infrastructure. The aim is to surprise people by showing what quite meaningless information will transform into.
We analyzed Apple’s privacy statements and got ideas from academia, but it remains our own thought experiment – as it often is the case with new media and big data. Various approaches come together in our blog: videos, texts, lists, tables, and – most importantly – visualizations such as mind maps, flow charts, and an interactive PowerPoint presentation. Using “Home” creates a flow of data. Therefore, the best way to visualize this is through arrows.
The visualizations illustrate which sorts of data is sent out by using the app. All this information is about the user’s offline behavior (Weinberg et al. 618) – “previously inaccessible parts of people’s private lives” (Ziegeldorf et al. 2736). With each additional data set, the user can be identified better (Weber 623).
-
The Output
Now, we present our blog, explain the ideas behind every post, and outline how they were realized. We used WordPress to create a blog because it is an easy, yet efficient tool. Moreover, the blog format matches our project because it is possible to include different kinds of media in an open, playful approach. As WordPress blogs usually do not show up on the first pages of Google search results, we tried tackling this problem by search-optimizing the title of our blog: “https://applehomedataprivacy.wordpress.com” includes the most important keywords which people use who are interested in this topic.
2.1. “What is the Problem?”
As a starting point, problems around privacy, the internet of things, and smart home devices are explained in easy terms to get the visitor’s attention and to raise his awareness for the existence of the problem. Like all our blogposts, it also links to the next steps. This treasure hunt principle is used to keep visitors interested. It is especially suitable for blogs with several posts, which have a less constrained structure than ordinary websites. The blog is also structured into categories (“The Project”, “Privacy”, “Appendix”) and subcategories, but can be explored easily without them due to the links from one article to another. Because of the simple and appealing titles “What is the problem?” and “What is Apple’s ‘Home’ app?”, visitors will most likely begin with these posts anyway.
2.2. “What is Apple’s Home App?”
This posts features a YouTube video explaining how the app works. Technical matters can be explained more easily in videos. The amount of “How to…” videos on YouTube shows that many people like the video format for such matters. There is an additional link to a comprehensive article on the background of the app for people who want to know more. Apart from that, this introduction is supposed to be as simple as possible to not frighten off less tech-affine visitors
2.3. “Apple’s Privacy Statements with regard to the Home App”
This post deals with Apple’s privacy policy, as found on their website. We wanted to clarify these statements because they seemed quite vague. By dividing the policy in a more general statement about privacy and a part regarding the consequences, the policy becomes clearer. Lastly, the statements and consequences are interpreted specifically concerning the app.
2.4. “Mind Map of all Data”
The mind map created with Coggle gives an overview of all the data that is possibly sent out while using “Home.” It shows various devices mentioned on Apple’s “Home” website as well as rooms and scenes. They are in different colors to trace back data on the right side of the mind map to the device, room, or scene. The word clusters at the end of the arrows show patterns and the more often one kind of information appears, the clearer it may get.
For example, there is a lot of information generated on the user’s daily routine: The way user’s handle locks indicate the time they are not home. With the help of this data, other clusters get clearer, too. Owning many security devices could mean that the user is anxious – or rarely in his house. If the daily routine shows that he often is at home, the data hints more towards being anxious.
In the end, this graphic combines two kinds of visualizations: mind maps and word cluster diagrams. By looking closer at it, quite specific information on which data is sent out can be seen. But this combination of many words and arrows also makes users realize the overall amount and the complexity of the data.
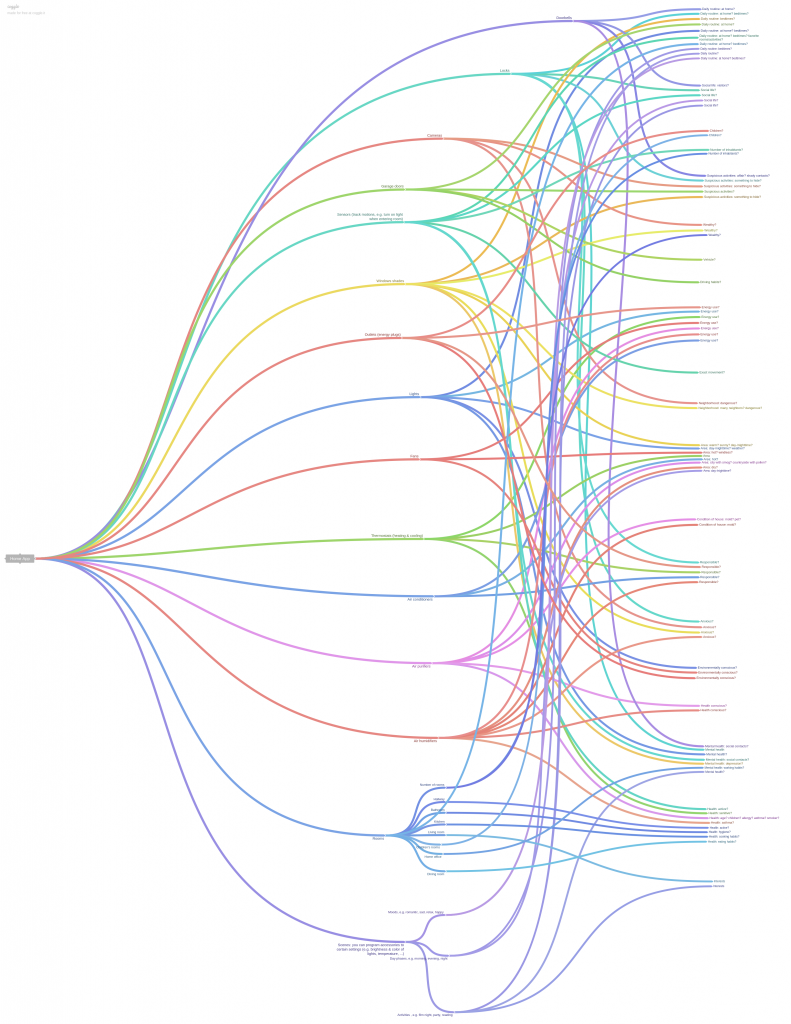
Mindmap of all data concerning the Home app (a larger image can be found on our blog)
2.5. Flowcharts
The flowcharts created with “draw.io” show different scenarios and make concrete what data is generated. It starts with “Flowchart of a Home app user”, a general visualization of the data flow, containing all the possible devices that are mentioned on the “Home” website. To make the data flows less confusing and more concrete, we included an experiment with a certain user and scenes, for instance the “Good Morning Scene Flowchart”. This results in a set of data which contributes to our aim of raising awareness because users are able to identify themselves with this outcome instead of rather abstract visualizations.
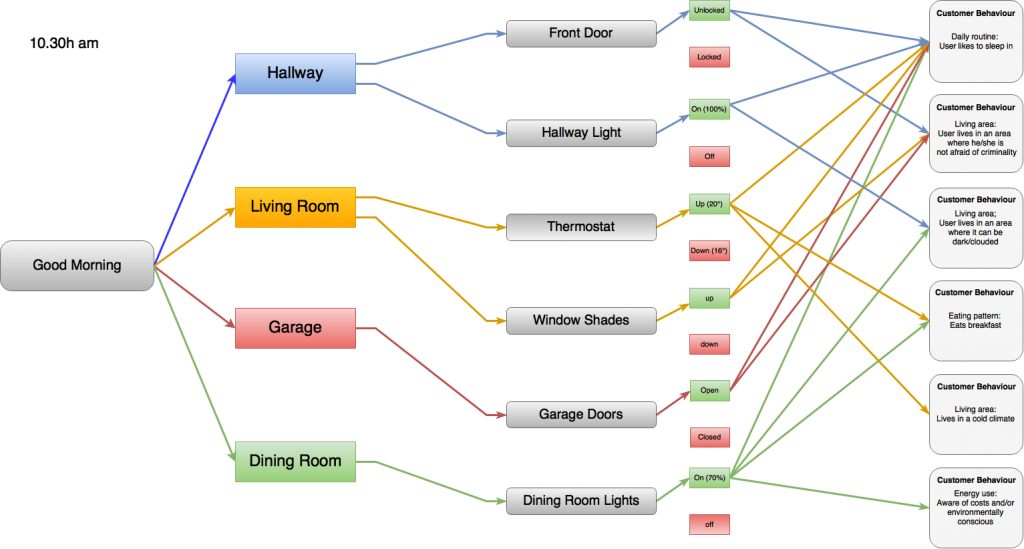
Good Morning scene flowchart
2.6. “A day with the App: from ‘Home’ to ‘Home -1.0’”
In order to build a remake of “Home”, an interactive interface was created. This shows several dynamics, information flows, and what Philip Agre calls “grammars of action” (745), like the possibility to activate or deactivate particular scenes.
We chose a traditional but effective application: Microsoft PowerPoint. This program offers the possibility to build an interactive interface using animations on different objects, accompanied by arrows and guiding texts to reveal the hidden infrastructure. By deconstructing the app’s interface into different objects (buttons, signs, texts, images, etc.), we built a dynamic prototype, instead of a static blueprint of the original interface. The user can tap his way through the interface to get an idea.
2.7. “Who is Interested in the Data?”
The blogpost “Who is interested in the data?” is a list. Because there are many different actors, a list gives a better overview than a regular text. Visitors can browse it and it makes reading more diverting. The question who is interested in the data from Apple’s “Home” app has not been thoroughly discussed yet among scholars. This is why we extracted information from several sources: scholars writing about the internet of things, Apple’s terms and conditions, news articles on Apple’s privacy issues, and our own visualizations.
2.8. Appendix
Throughout the blog, scholars are cited. While this is sufficient to know for the average visitor, more committed ones can have a look at a detailed reference list. This can also be understood as a recommended reading list. The post “…the project & its creators” provides some background information. A detailed description of the production process can also be found on our blog.

-
Contribution to Current Debates
Looking at the history of media artefacts, an increasing amount of user agency seems to accompany the introduction of those devices. In chronological order, artefacts like the remote control, the video recorder, and the mobile phone owed their newness to their advanced qualities when introduced into society (Hansen 172). For example, the remote control gave the user power to zap between channels from their seat, while the video recorder offered the possibility to play programs back and forward. The newness of these once new media in terms of materiality, technicity, as well as storage, transmission, and processing of data results in new user experiences, especially in terms of control.
It is remarkable that a significant part of the academic debate around control within media studies is about control over the citizen, rather than control of the citizen. Social theorist Michel Foucault described a transition from societies of sovereignty to disciplinary societies, and uses the Panopticon as a metaphor to gain control over a complex surveillance society, which is based on discipline and surveillance similar to the modes of tempering prisoners (201). According to philosopher Gilles Deleuze, these disciplinary societies are nowadays replaced by societies of control in which different control mechanisms are no longer based on discipline, but on “dividualisation” (4), which involves the dissolving of individual identities into distributed information networks (Galloway 86). Media professor Alexander Galloway noticed that, just like the regulation by protocol within technological networks, protocol also exists among actors in the social space (86), and therefore the control mechanisms described by Deleuze are protocological by nature.
For this project, we took into account the notion of what Mark Deuze in his second lecture of the course “Media Defined” described as the ultimate but illusory dream of control, to which we most likely come closer following the tradition of increasing feeling of user control due to newly introduced media artefacts. We emphasized feeling of because well-known research by psychologist Ellen Langer showed that the perceptions of control are often illusory (327). Moreover, going back to control over the user, Brandimarte et al. noticed that “more control can sometimes lead to less privacy” as users give away (maybe unknowingly) more and more of their personal data, although they still feel the power is in their own hands (15, emphasis original).
This project breaks through this illusion of control by offering a critical approach to Apple’s new “Home” app. Since smart devices are seemingly giving users the power to control their homes from wherever they want, “Home” is the ultimate case to expose some controlling activities of the companies behind.
Our blog also picks up the question what happens with the user’s data in times of the internet of things and smart home devices. Data dissemination does happen as this example shows:
“From December 1, 2012 to May 31, 2013, Apple received between 4,000 and 5,000 requests from U.S. law enforcement for customer data. Between 9,000 and 10,000 accounts or devices were specified in those requests, which came from federal, state and local authorities and included both criminal investigations and national security matters. The most common form of request comes from police investigating robberies and other crimes, searching for missing children, trying to locate a patient with Alzheimer’s disease, or hoping to prevent a suicide.” (Hattersley)
Because data from app also covers offline behavior and can accumulate a lot, this problem reaches a new level. Scholars mention several actors that may be interested in data from the internet of things. We elaborated on their ideas and added several actors from the particular case of the “Home”:
- Businesses (Perera et al. 36; Ziegeldorf et. Al 2735)
- Insurance companies (Maras 103).
- Banks (Maras 103).
- Employers (Maras 103).
- Landlords
- Law enforcement (Ziegeldorf et al. 2737)
- Courts
- Governments (Ziegeldorf et al. 2735), including intelligence agencies (Timm)
- Criminals (Ziegeldorf et al. 2737, Perera et al. 36).
Plus, there always remains the risk of hacking (Weinberg et al. 620; Maras 100). And then, anyone might get the information (Timm).
The dissemination of this data is especially dangerous because this data has to be interpreted and thus the information from it is not always accurate. This creates another risk: false accusations. Especially in very sensitive cases such as checking alibis and eligibility for insurances, misinterpretations can have severe consequences. With computers getting more autonomy in data analyzation and decision-making, human common sense does not play such a role anymore – although it may be necessary in these cases (Ambasna-Jones).
To sum up, our project picks up a new aspect of the internet of things: smart homes. It has shown how smart devices generate big data that can cause a loss of privacy in offline life. All-encompassing apps like Apple’s “Home” are the latest developments towards a mere illusion of control and “Home -1.0” wants to raise awareness of this.
By Rick Bijsterveld, Michel Blonk, and Vincent Buss
Bibliography
Agre, Philip. “Surveillance and Capture: Two Models of Privacy.” Information Society 10.2 (1994): 101-127.
Ambasna-Jones, Marc. “The Smart Home and a Data Underclass.” The Guardian 3 Aug. 2015. The Guardian. Web. 14 Oct. 2016.
Brandimarte, Laura, Alessandro Acquisti and George Loewenstein. “Misplaced Confidences: Privacy and the Control Paradox.” Social Psychological and Personality Science 4.3 (2013): 1-22.
Betters, Elyse. “Apple HomeKit and Home App: What Are They and How Do They Work?” Pocket-lint. N.p., 13 June 2016. Web. 16 Oct. 2016.
Deleuze, Gilles. “Postscript on the Societies of Control.” L’Autre Journal 0.1 (1990): 3-7.
Deuze, Mark. “Media Defined.” Media Life. University of Amsterdam. Amsterdam, 11 February 2015.
Deuze, Mark. Media Life. Cambridge: Polity Press, 2012.
Foucault, Michel. “Panopticism.” Discipline and Punishment: The Birth of the Prison. Vintage: New York, 1975. 195-228.
Hansen, Mark. “New Media.” Critical Terms for Media Studies. Eds. William Mitchell and Mark Hansen. Chicago: University of Chicago Press, 2010. 172185.
Hattersley, Lucy. “Are We Giving Too Much Info to Apple? We Look at Apple’s Data Collection and Privacy Policy.” Macworld UK. N.p., n.d. Web. 15 Oct. 2016.
Langer, Ellen. “The Illusion of Control .” Journal of Personality and Social Psychology 32.2 (1975): 311328.
Maras, Marie-Helen. “Internet of Things: Security and Privacy Implications.” International Data Privacy Law 5.2 (2015): 99–104. idpl.oxfordjournals.org. Web.
Perera, Charith et al. “Big Data Privacy in the Internet of Things Era.” IT Pro (2015): 32–39. Print.
Shaw, Jonathan. “Why ‘Big Data’ Is a Big Deal.” Harvard Magazine. N.p., 18 Feb. 2014. Web. 15 Oct. 2016.
Sicari, S. et al. “Security, Privacy and Trust in Internet of Things: The Road Ahead.” Computer Networks 76 (2015): 146–164. ScienceDirect. Web.
Timm, Trevor. “The Government Just Admitted It Will Use Smart Home Devices for Spying.” The Guardian 9 Feb. 2016. The Guardian. Web. 14 Oct. 2016.
Weber, Rolf H. “Internet of Things: Privacy Issues Revisited.” Computer Law & Security Review 31.5 (2015): 618–627. ScienceDirect. Web.
Weinberg, Bruce D. et al. “Internet of Things: Convenience vs. Privacy and Secrecy.” Business Horizons 58.6 (2015): 615–624. ScienceDirect. Web. SPECIAL ISSUE: THE MAGIC OF SECRETS.
Ziegeldorf, Jan Henrik, Oscar Garcia Morchon, and Klaus Wehrle. “Privacy in the Internet of Things: Threats and Challenges.” Security and Communication Networks 7.12 (2014): 2728–2742. Wiley Online Library. Web.
Other
“Privacy Policy.” Apple. 2016. 9 October 2016. <https://www.apple.com/privacy/privacy-policy>
“Home.“ Apple. 2016. 19 September 2016.<http://www.apple.com/ios/home/>