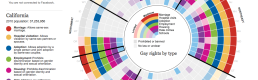
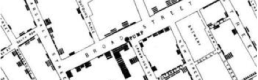
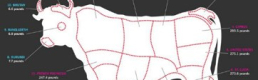
Using map projections in data visualizations
In an era of internet users actively creating their own content, easily accessible tools are available for the public to create their own data visualizations. Applications like Many Eyes or Tableau Public give statistic enthusiasts the appropriate possibilities to...