Give us your data and you will never walk alone
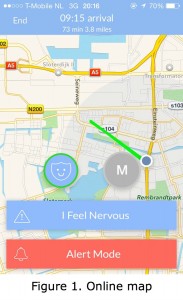
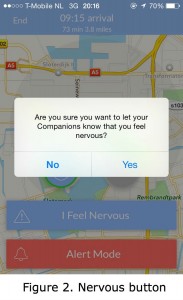
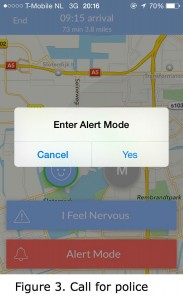
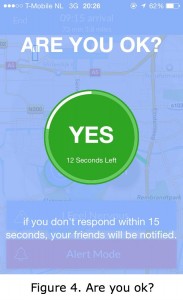
Last week, five students from the University of Michigan launched (Mashable, Tech Times, Business Insider) a smartphone application called Companion. This application enables users to be accompanied by their contacts to virtually walk them home at night. The so-called “companion” can then keep track of the user’s journey via GPS that shows his exact location on an online map (see figure 1). The application provides the user with options, such as: calling for help whenever they don’t feel comfortable by tapping the ‘I feel nervous button’ (figure 2). Another option for users is to tap the ‘call police’ option in case of an emergency (figure 3). The companion is given the option to ask whether the person heading home is ‘ok’. The user has to respond to this question within 15 seconds (figure 4). This app would have been very useful to me at the time that I used to live in a small town and had to, through the Dutch polders, walk or bike home late at night.
Since the emergence of digital devices that are always in connection with the Internet, people have been critical and hold back whenever applications ask for access to their personal data. While these apps use our data partly for our convenience, it is not longer a secret that they also share it with third parties in order to benefit from it economically (Culnan & Bies 2003). Browsing and location history are two prime examples of such data that is economically interesting. These sets of data that are being captured, also called data trails, are often not the intention of the user, but part of how the application can make profit. What is interesting about the Companion application though, is the fact that people intentionally leave their trail of data behind. In return they expect a particular service from this app. This application offers users a service to make them feel safer while heading home late at night. Therefore this process of data tracking can be seen as a solution to a big problem within our society.
Philip Agre discusses in one of his papers that the notion of privacy is “particularly significant right now, given the rapid emergence of new technologies and new policy issues around privacy” (740). Here he contrasts two different models of privacy: the surveillance- and the capture model. The surveillance model is coherent with Foucault’s notion of self-discipline, where people are expected to behave because they know they’re being watched. In contrast, the capture model is focused on the so-called ‘capta’. The capta is the user’s input, which is taken up and processed by an automated system without the user being aware of it. Therefore, this new model of privacy is less visible than the traditional model. Individuals are being guided by what Agre coined the ‘grammar of action’, which is embedded in the system itself and gives directions to the user according to a set of rules. These rules are standardized and ensure that pre-specified tasks are carried out based on criteria (744).
Taking a closer look at the Companion app, we can see some elements that fit the before mentioned capture model. The application captures data in order to create a specific profile of the user’s personal data and his location history. However, in contrast with the capture model, the user intentionally shares his current location with the companion. Specific buttons that trigger actions, such as calling the police or sharing your location with a companion, help the user to become more aware about what and when certain data is being shared. So what is different in this app is that, at least on the surface, it looks like the user is more in control of deciding whom to share their data with. However, this application is not transparent in showing how the data is really shared.
One way to obtain more insights in how the user’s data is being re-produced, is by looking at their privacy policy from their website. They claim to collect personal data such as “Cookie, Usage data, Phone number, General activity data, Gender, Geographic position and Various types of Data”. (Companion) They also mention sharing this data with third parties, such as Google.One can argue that on the one hand this application is created for safety purposes, but on the other hand all data of the user is being shared and therefore controlled by companies that have, on the surface, nothing to do with the whole safety notion. Therefore, rather than being a safety app for the user’s convenience, there lies a certain economic motivation beneath the surface that uses the data produced by the user for its own commercial interests. This can be linked to what Roger Clarke discusses in one of his articles on how the individual is now living in an era of data surveillance, which is economically driven (1994).
Further research has to focus more in depth on a new understanding of privacy. The shift that is in conflict with the notion of privacy is not very new, but here the user intentionally leaves a trail of data behind to benefit from particular services. We know that big brother is watching us.
References
Agre, Philip E. “Surveillance and capture: Two models of privacy.” The Information Society 10.2 (1994): 740-760.
Calpito, Dave. “Walking Home Alone? ‘Companion App’ Will Make Sure You Get To Your Destination In One Piece.” Tech Times. 2015. 8 September 2015. <http://www.techtimes.com/articles/82213/20150905/walking-home-alone-companion-app-will-make-sure-you-get-to-your-destination-in-one-piece.htm>.
Clarke, Roger. “The digital persona and its application to data surveillance.” The information society 10.2 (1994): 77-92.
Culnan, Mary J., and Robert J. Bies. “Consumer privacy: Balancing economic and justice considerations.” Journal of social issues 59.2 (2003): 323-342
Foucault, Michel. Discipline and punish: The birth of the prison. Random House LLC, 1977.
Russon, Mary-Ann. “A new app that lets users’ friends ‘virtually walk them home at night’ is exploding in popularity.” Business Insider. 2015. 8 September 2015. <http://www.businessinsider.com/campanion-app-surging-in-popularity-2015-9?IR=T>.
Strange, Adario. “This app gives you a virtual security guard to walk you home.” Mashable, 2015. 8 September 2015. <http://mashable.com/2015/09/05/virtual-security-guard-app/#Ycjt9Io5CPkZ>.