Blind Spots: The value of information about cloud services for user empowerment.

“Cloud” – a word that suggests the promise and experience of accessing files from anywhere you choose, much like pulling it down from the sky. However, when we think of the verb “to cloud”, it means ‘to make less clear or transparent’. This interpretation seems to have a closer connection to our reality, where the cloud is not something that floats above our heads, but consists of a complicated network of data centers that store our information. Yet, as long as we can conveniently store and access our data, we may not think about the reality of our data’s whereabouts, what happens to it, or how and by whom it is being accessed. The analogy of the cloud obscures the infrastructures that make the storage of data possible (Niederer and Taudin Chabot 2).
The reality
Cloud computing broadly refers to “both the applications delivered as services over the internet and the hardware and systems in the data centers that provide those services” (Ambrust et al. 50). Where data used to be stored on user’s devices, it is now being kept in large data centers made up of thousands of servers and is only accessible through a web-interface. The whole architecture is then controlled by a centralized entity: the cloud provider (de Filippi 49). However, this reality of the cloud may not be fully understood by its users (Parks 370). The obscurity surrounding the cloud diminishes the capacity of individuals to make informed, meaningful choices about their data and undermines their autonomy. In an era where data yields power, the control of information, or lack thereof, challenges a user’s capacity for self-determination (Cohen 2).
Blinded
In this technological landscape where users are invited to share their personal data in return for access to digital services, it is unlikely for individuals to give meaningful, voluntary consent to the data sharing and processing activities entailed by Big Data analytic techniques (Acquisti, Brandimarte, and Loewenstein 509). Users struggle to understand and manage their privacy relations with the hundreds of digital service providers that they interact with online and they find it almost impossible to adequately assess the risk of harm in a
series of isolated actions (Solove 1891, 1891). Taking all of this into account, we argue that the ambiguous information presented by service providers about the infrastructure of the cloud threatens the user’s right to self-determination and therefore, that more transparency on these matters will enhance user empowerment.
So what?!
Smart technology has become so intertwined with our lives that it is not an addition as much as a part of it. However, the notion that these electronic companions and their assets are impartial bystanders, has long been repudiated. By increasing our involvement with smart technologies, not only do we increase our dependability on the technologies themselves, but also on the actors behind them (Rieder 17).
Losing control
Technological evolvement rendered the possibility for communication limitless, and consequently our need to access our data increased. The cloud fulfills that need. It allows users to access data anyplace, anywhere, anytime. In essence ‘the cloud’ is a physical infrastructure of data centers with virtual applications running in the foreground. These elements are put in one neat package by providers and offered as a service (Erdogmus 5). In this structure users do not host their data on a private server as they used to, they merely interact with their data using devices like tablets, smartphones, and computers. The set-up allows for less control at the level of the users and greater control for the providers (de Filippi 47). The allocation of control allows for new stakeholders such as data-driven businesses or even governments seeking information on their citizens. Moving from physical hard drives to relying on companies to handle information, questions about privacy, security, control and ownership multiply (Kshetri 376, 383). These uncertainties demonstrate the obscurity of the cloud that limits the user’s power for self-determination.
User Empowerment
According to Friedman and Nissenbaum, self-determination consists of the capability to create your own objective and subsequently have the capacity to decide in a way that will help you reach it. If this condition is met, an individual is considered ‘autonomous’ (466). To make a well-considered decision, it is important to know what the different choices entail and for this reliable information is crucial (Cohen 8). The obscurity regarding cloud services then diminishes a user’s autonomy as it enhances the possibility for data to move without a user’s permission or choice. In this context, providing users with reliable information to help them make a more deliberate choice and increase their control over data in the cloud, can be considered ‘user empowerment’ (Stark and Tierney 4). Hence, user empowerment can be enhanced by creating more awareness and knowledge about the structure of the cloud (Piderit and Nyoni 8).
Taking the reins
Are we ever more than twenty feet away from a smart device? We want to have the universe within our reach and cloud services can afford that to us. However, this does not mean that we have to surrender blindly to the objectives and ideologies of the provider. With access to reliable and understandable information, we can regain autonomy over our data. As this technology is a permanent part of our lives, ‘user’ is not just a term anymore but a constant state of being. Consequently, there is little that seems more relevant than ‘user empowerment’, and in order to be empowered, we need to be informed.
Empowerment through visualization
“The biggest challenge of the Petabyte Age won’t be storing all that data, it’ll be figuring out how to make sense of it” (Horowitz 2008).
Although the devices that help manage our data are an integral part of our lives, making sense of the structure that they are part of can be a challenge. By taking an element of the cloud out of obscurity and making it observable, we can enhance our understanding of it (Mattern 6). An alternative representation as such encourages users to form a new and critical perspective (Parks 356). Depicting the data in a visualization should thereby enhance the user’s awareness.
Virtual Limits
The use of visualizations to inform the public is not new, according to Kennedy et al. it can be traced back to the mid 19th century (6). However, its long history does not mean that the data representation is necessarily clear, impartial or good. Visualizations are the product of choices by designers, organizations or others actors, and this has an impact on their content (Kennedy and Hill 5). It is also important to consider that users may misinterpret the intention of the visualization altogether: Kennedy and Hill describe that there is no guarantee that visualizations are decoded and interpreted equally in ways that were originally intended (5).
A visual advantage
When visualizations are distributed on a large scale, they have the capacity to influence the perception of users, viewers or whatever public they encounter. It can, therefore, be said that they bear a certain amount of power (Barnhurst 79). We intend to use this power to help make sense of cloud services and establish more autonomy for users. The belief that visualizations create a bigger understanding of data and thus benefit the public is one that we share with multiple designers. Designers often intend to create more clarity of information, making the data more accessible to the larger public through visual representation (Kennedy et al. 8). As such, a visualization can provide a counterbalance to the power that cloud service providers hold (Kennedy et al. 11).
Providers do not only control their user’s data, they also dictate the available information about their services and the way they communicate about this. In these circumstances, there is an “unequal distribution of power over data” at the cost of the user (Van der Velden 11). A visualization that enhances the user’s knowledge of cloud services can, therefore, be regarded as a tool for user empowerment.
Finding the Blind Spots
In order to demonstrate the ambiguity of the cloud, we analyze three providers of cloud storage services: Google Drive, Dropbox and iCloud, utilizing the framework “Enhancing User Trust in Cloud Computing Applications” (Piderit and Nyoni 11). The framework assesses a cloud service provider using seven factors called “Critical Successes Factors” over five stages to show how a cloud provider can enhance user trust as detailed below in the model. We choose this model because Piderit and Nyoni claim that their objective ‘to enhance user trust’ can be reached by creating and ‘understanding of the dynamics’ of cloud services. Since we argue that clear information can enhance user empowerment, this model is an appropriate basis for our research.
Withal, our qualitative analysis is not meant to be exhaustive or conclusive, rather, it is meant to answer the question how we can empower users through examining which information is provided or obscured by cloud service providers. Therefore, we will only apply the first stage of the framework which is “knowledge”, as this stage is most relevant to our conducted analysis. Yet to obtain the full picture about a cloud provider, the framework should be applied to the five stages as suggested by Piderit and Nyoni (10).
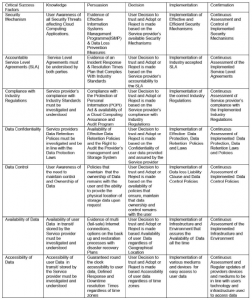
Model: Enhancing User Trust in Cloud Computing Applications
De-clouding Cloud Services
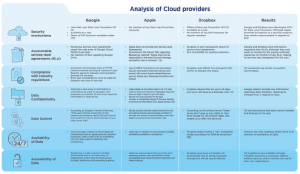
Upon comparing the trust model to Google, Apple and Dropbox’s business models (detailed results can be viewed here), what is most revealing is what was left out, thus being the lack of information provided to the user. Although Google and Dropbox openly reveal their Service Level Agreements (for paying services), Apple does not have an open Service Level Agreement, regardless of payment models. Apple reveals a contradiction towards the trust model due to their shortcoming in accountability and transparency (SLA), yet its services continue to be used and popularized.
Company interests
What is also notable is how the trust model showcases each company’s interests. Google’s multiple SLA’s, which display how extensive their cloud services are, making it an ideal service for business, are looking to expand their communication practices and also require dependable cloud security. Apple is focused on their own products, making umbrella statements towards the security measures across their products and apps. Apple products function across the same operating system, which limits 3rd party intervention and centralizes security. Since Dropbox offers business services too and is very in-depth about their SLA’s and their security features, it is an ideal alternative for businesses who are not interested in using Google’s services. It is important to mention that information security and company responsibilities are enforced and directed towards paying customers, meaning that users with free accounts may hold companies less accountable. For example in the event of data loss.
Revelations
As being a ‘user’ has become part of our identity, ‘user empowerment’ has never been more relevant. This empowerment can be influenced by the provision of information since reliable information is needed to make well-considered decisions and determine our own faith. Obscurity about cloud services endangers this capacity for self-determination. We should be able to decide what happens to our data and therefore we need knowledge about the dynamics and structure of the cloud. Revealing the blind spots in information about cloud services can add to that knowledge.
Use for a blindfold
Drawing from our results, we pieced together existing blind spots as they reveal themselves when comparing cloud companies statements to existing models of trust between users and providers. The leading concern here is that cloud companies do not consistently disclose specific important information to the user upfront, such as when companies leave out Service Level Agreements or not distinguish their responsibilities towards a free account or a paid account. The constant change and evolution of technology may obscure a company’s responsibility to disclose information or inversely, one may take advantage and benefit from user unawareness, meaning that the user is left to their own devices when deciphering given information in order to make educated and properly informed decisions.
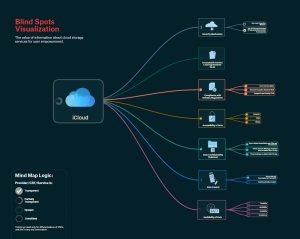
Mind Map
By visualizing the blind spots we contended to enhance a user’s perception while providing empowerment through knowledge and information. Mattern described the importance of visualizing these blind spots, in arguing that infrastructures and landscapes are always in flux, thus requiring us to constantly adjust our perceptual capabilities and create parameters in order to comprehend and shape those landscapes (16). We chose the Mind Mapping method in visualizing the blind spots due to its simplicity as shown below. With our visualization, we aim to help users understand what is at stake when it comes to storing their data in the cloud, by demonstrating where the providers are transparent and where they are
opaque. Mapping the blind spots are not meant to be exhaustive, rather, it is meant as a prototype that can scale to larger or smaller capacities when inspecting cloud service providers.
Clarity
Regardless the method, any visualization represents the ontological complexity of various forms of infrastructures, which encourages us to translate heightened knowledge into real meaningful action. By representing the blind spots of cloud services in a visualization, users can be informed and thus; empowered.
References
Acquisti, Alessandro, Brandimarte, Laura, and George Loewenstein. “Privacy and human behavior in the age of information.” Science 347 (2015): 509–514.
Ambrust, Michael, et al. “A View of Cloud Computing.” Communications of the ACM 53.4 (2010): 50-58.
Barnhurst, Kevin. Seeing the newspaper. New York: St. Martin’s Press, 1994.
Cohen, Julie E. “Between truth and Power.” Eds. Mireille Hildebrandt and Bibi van den Berg. Freedom and Property of Information: The Philosophy of Law Meets the Philosophy of Technology. New York: Routledge, 2014. 1-20.
Erdogmus, Hakan. “Cloud Computing: Does Nirvana Hide behind the Nebula?” IEEE Software (2009): 4-6.
De Filippi, Primavera. “Ubiquitous Computing in the Cloud: User Empowerment vs. User Obsequity.” Eds. Jean-Eric Pelet and Panagiota Papadopoulou. User Behavior in Ubiquitous Online Environments. Pennsylvania: IGI Global, 2014. 44-63.
Friedman, Batya and Helen Nissenbaum. “Software Agents and User Autonomy.” Presented at the AGENTS ‘97: Proceedings of the first international conference on Autonomous agents (1997): 466-469.
Hill, Lucy and Helen Kennedy. “The Pleasure and Pain of Visualizing data in Times of Data Power” Television and New Media (2016): 1-14.
Horowitz, Mark. “Visualizing Big Data: Bar Charts for Words.” WIRED. 14 October 2017.
<https://www.wired.com/2008/06/pb-visualizing/>
Kennedy, Helen, et al. “The Work That Visualisation Conventions Do.” Information, Communication & Society 19 (2016): 715–735.
Kshetri, Nir. “Privacy and security issues in cloud computing: The role of institutions and institutional evolution.” Telecommunications Policy 37 (2013): 372-386.
Niederer, Sabine and Raymond Taudin Chabot. “Deconstructing the Cloud: Responses to Big Data Phenomena from Social Sciences, Humanities and the Arts.” Big Data & Society 2.2 (2015): 1–9.
Mattern, Shannon, “Infrastructural Tourism,” Places Journal (2013). 8 October 2017. <https://doi.org/10.22269/130701>
Parks, Lisa. “”Stuff You Can Kick”: Toward a Theory of Media Infrastructures.” Between Humanities and the Digital. London: The MIT Press, 2015. 1–20.
Piderit, Roxanne and Tamsanqa Nyoni. “Enhancing User Trust in Cloud Computing Applications.” CONF-IRM 2016 Proceedings 50 (2016).
Rieder, Bernhard. “Beyond Surveillance: How Do Markets and Algorithms ‘Think’?” Le Foucaldien 3 (2017): 1-20.
Solove, Daniel J. “Privacy self management and the consent dilemma.” Harvard Law Review 126 (2013): 1880–1893.
Stark, Luke and Matt Tierney. “Lockbox: mobility, privacy and values in cloud storage.”
Ethics and Information Technology 16 (2014): 1-13.
Van der Velden, Lonneke. “Forensic Devices for Activism: Metadata Tracking and Public proof.” Big Data & Society 2.2 (2015): 1-14.