Cybercascades in Twitter
Introduction
After the attacks on September 11 2001 America started their “War on Terror”. One of the targets in this war was of course Iraq, because Iraq was creating Weapons of Mass destruction (WoMD). This “news” spread around the world like a burning fire, and soon a lot of people just assumed Iraq was dangerous and should be stopped.
The story above is an example of a social cascade, a massive snowball-effect of information that gets spread around without knowing anything about the truthfulness of the information. The WoMD-story is a so-called reputational social cascade, in where people indiscriminately believe the words coming out of a person with high(er) value, in this case the president of the United States. (Barton, p.13)
Cascades exist in all social networks, and because of this, also in Social Network Sites. The term Cybercascades is introduced by Cass Sunstein in 2001 and are digital cascades which are being driven by information. (Sunstein, 2001: p.83) A short example of a cybercascade is the chain-forwarding of hoax e-mails, where people are lead to believe their ‘e-mail account will get deleted’ or ‘they are going to have bad luck’, so they send the e-mail to thousands of people.
An important part in these digital cascades is played by the existence of the “small world model”; a model where groups of people are created based on interests, meanings and purposes. In these groups it is the opinion leader who is being followed by the other members. They are the centre of a large group of people, which we use “as shortcuts and filters for our own decision-making”. (Krebs, 2005: p.4)
With this being said, it can be said that SNS and microblogging-tool Twitter contains a lot of cybercascades. All the components are there: the social environment, the opinion leaders and the means of information-spreading.
The basic means of communication in twitter is of course ‘tweeting’ itself, sending short messages up to 140 characters to others, but Twitter has also incorporated something called a “retweet” and a hashtag (#). A retweet is a copy of a previously send tweet, containing at least the original message and its author and sometimes an extra few words. It is said that structurally, retweeting is the Twitter equivalent of email forwarding. (boyd, 2010: p.1) A hashtag is a word after a ‘#’ character and can be included in tweets to make it more searchable and give it a subject. Tweets can contain many hashtags, limited only by its maximum characters.
The opinion leaders are present in the form of people with many followers. As boyd says, “spreading tweets is not simply to get messages out to new audiences, but also to validate and engage with others” (boyd, 2010:p.2) Tweeps (people who twitter) want to validate themselves, which can be done by following a certain people and tweeting interesting stuff.
These are all ways to get a cascade going. Where a retweet is an (expanded) copy of a message, a hashtag is a global sort of subject, e.g. #fail, #goodmorning and the current popular #newtwitter. All these can be spread across twitter and the internet in a single click.
#Newtwitter
To show an example of a cybercascade in Twitter, I will look at the current popular #newtwitter. Statistics in April 2010 show Twitter had 105,779,710 registered users worldwide, and 300.000 new users were signing up on it per day. Also, all these users tweet an average of 55 million tweets a day. This means that 55 million pieces of information, some useful and other useless, gets published for other people to read.
In order to look at a cybercascade in Twitter, we have to be able to show and map these massive amounts of data. Luckily there already are a lot of tools to do this.
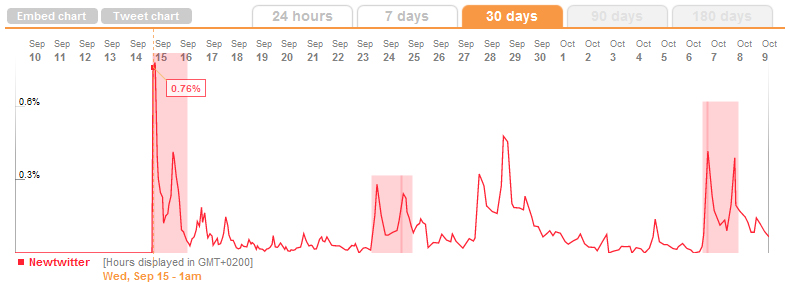
The tool that showed best what I wanted to show is Trendistic, a website where you can look up any word and get a visually appealing Tweet chart, showing the word’s trending of the current day, the last week or the last month. When I looked up the word “newtwitter”, it showed the following result:
As the graph shows, the first message of it appeared on 15 september 2010. This was the day Twitter announced their upcoming new layout and design. A total of 0,76% of all tweets contained the word “newtwitter”, which declined fast after the 15th. Still, it is an ongoing trend, and was popular again on both september 28th and october 7th. These are all messages that started by a single person or a few people, and got tweeted and retweeted on a large scale.
Justin Bieber
Another good example of a more continuous cybercascade is Justin Bieber. In a previous post I wrote that of all Twitter-servers, 3% is “controlled” by Justin Bieber. With more then 5 million followers, his account receives more then 60 replies per second for a while after he tweets. When searched for in Trendistic, it showed the following graph:
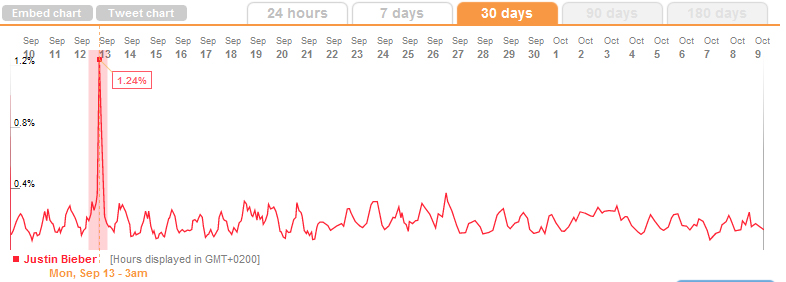
There are alot of spikes in the curve, with an absolute peak on 12 september after the VMA’s.
Conclusion
In all social environments there is an opportunity for information to cascade; to be spread around the world with a snowball-effect. In microblogging tool Twitter this cascading exists in the form of trending topics and is made possible by both retweets and hashtags. This combined with its millions of users there is a good probability for a cybercascade to begin and to be kept alive continuously, as shown in the Justin Bieber graph. *sigh*
References
Barton, April M. 2009. “Online Cascades”, Minnesota Journal of Law, Science and Technology Forthcoming (2009). http://works.bepress.com/april_barton/7
boyd, danah, Golder, Scott, and Lotan, Gilad. (2010). Tweet Tweet Retweet: Conversational Aspects of Retweeting on Twitter. Proceedings of HICSS-43 .Kauai, HI January 5-8.
Krebs, Valdis. 2005. “Its the Conversations, Stupid! The Link between Social Interaction and Political Choice.” In Jon Lebkowsky and Mitch Ratcliffe (eds.), Extreme Democracy.http://www.extremedemocracy.com/archives/2004/08/chapter_9_its_t.html
Sunstein, Cass. 2001. “Republic.com”. Princeton: Princeton University Press, 51‐88.