Netneutrality: a product of the control society?
Early May 2011, Dutch telecom provider KPN announced her plans to block certain mobile Internet services like Voice over IP, in order to offer these services for an additional fee. One of the reasons for these measures is the decline of profit generated from regular text messaging and phone calls because of their online alternatives (Bits Of Freedom). After this announcement Vodafone also noted their plans of blocking certain services such as VoIP.
The plans of the telecom industry encountered criticism from consumers, government and companies. The European Commissioner of ICT, Neelie Kroes, announced an investigation about the possible blocking of data traffic. On 20 October the European Parliament understated the urgency of supervising net neutrality and noted the serious risks of ‘data discrimination’ (Webwereld). According to the French digital civil rights movement ‘La Quadrature du Net’ the European Parliament will make amendments to the European legislation to support the neutrality of the Internet (La Quadrature du Net).
Control society
Deleuze’s well-known essay “Postcript on Control Societies” from 1990 is defining a turning point of social formations. Deleuze describes that society has shifted from “disciplinary societies” to the “societies of control”. We have moved away from a society based on the confinement of institutions, and moved towards a society based on modulation, in a constant process of adjusting and deforming. (Deleuze 3) Society is no longer molded into an enclosed system of discipline, but a continuously modulating and flexible process with the emphasis on control. This has his consequences for the established institutions, like the education system or the factory. The modern individual is no longer subject to a fixed pattern, instead it shapes their own in a continuous process subject to variable rules and regulations (Deleuze 5).
Perhaps one of the perfect examples of the control society in operation is the Internet. A free flowing and distributed network of information. Alexander Galloway and Eugene Thacker make the analogy of an information freeway. The Internet does not enclose people, but instead it multiplies the means of control. (Galloway and Thacker 10). The Internet is not fixed in time or space, instead it is part of a continuous process of control through coded regulation. Galloway and Thacker describe these means of control as protocol –all the conventional rules and standards that govern the relationships in a network (Galloway and Thacker 5). Control in a network is therefore based and depending on protocol.
Technicalities of the Internet
To clarify how control exists in protocol and its relation to power, it is first important to address certain technicalities of the Internet. I will explain briefly how neutrality is inherent to the foundation of the Internet. The Internet as a digital network has a certain freedom encapsulated in the structure of the network. The first chapter of Galloway’s book “Protocol: How Control Exists after Decentralization” gives an explanation of how networks can be structured in three different types.
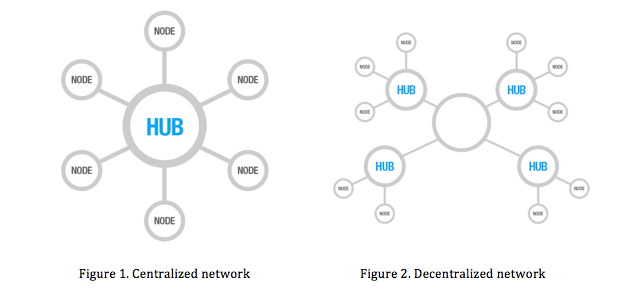
First the simplest form of networks, the decentralized network (fig. 1). Different nodes are not directly connected, and all traffic goes through one authoritarian hub. Galloway uses a specific institution as an example for a centralized network, the American court system. This system consists of a hierarchy that leads up to one central point of power (Galloway 31). The second network is the decentralized network (fig. 2), a multiplicity of centralized networks, where power is spread among multiple hubs. There is no hub in complete control over the network. Nodes are connected through various hubs. However, power is still not distributed equally in a decentralized network, for the hubs still have the power over the information traffic. (Galloway 31).
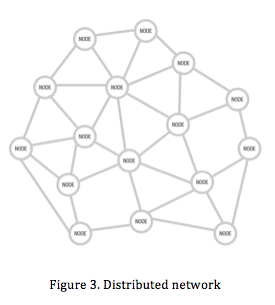
Thirdly, in the distributed network (fig. 3) all nodes are theoretically connected with each other without the interference of hubs. The power over information is therefore distributed equally. There are no central points that control the traffic of information. It has a flat hierarchy in which every node can operate independently (Galloway 38). The Internet is a distributed network. Therefore, the Internet has in itself no form of power over information. There is no central point through which information is being processed. Instead information is only subject to the rules of the network: the neutral treatment of information is coded the protocols. In the recent case of European net neutrality, it is important to understand that the neutrality of information on the Internet is based on protocol.
Using protocols to discriminate
The Dutch telecom providers are challenging at the level of protocols. To understand this we need to go more in depth on how protocols of the Internet function. In “Protocol, Control, and Networks” (2004), Galloway and Thacker describe how protocols operate on different levels of a network. Using the specifications from the “Requirements for Internet Hosts” they define four different layers of the Internet. (14).
- the application layer (e.g., Telnet, the Web);
- the transport layer (e.g., TCP);
- the Internet layer (e.g., IP);
- the link (or media-access) layer (e.g., Ethernet).
Each layer has its own protocols. The layers are nested, meaning that every layer interconnects with the preceding layers. For example, the application layer (the Web) is based on the transport layer (TCP), which in turn is based on the Internet layer (IP), which in turn is based on the link layer (Ethernet).
In our case study, the providers use protocols for another cause, to discriminate data. One of the to be blocked protocols is the “Voice over IP” (VoIP) protocol. According to the Federal Communication Commission this protocol designed to set a standard for the sending and receiving of digital audio signal (FCC.gov). The VoIP protocol is used by applications as Skype. Another threatened protocol is the XMPP protocol, used by text messaging services such as WhatsApp!. (XMPP.org) Both protocols are located at the application layer of the Internet. They are built on the transport and Internet layer of the network, the TCP/IP protocols that ensure a neutral, non-discriminative connection from node to node.
According to Stanford Law Professor Lawrence Lessig the role of an Internet provider is in the name: providing access to the Internet. Providers of mobile Internet should therefore be seen as part of the link layer. The plans of the mobile Internet providers are however based on specific protocols from the application layer of the Internet. In a way this debate is following the same trajectory as Lessig describes when mentioning the rise of broadband cable Internet.
“While the essence of the commons of the Internet was neutrality, and simplicity, the essence of what the broadband cable Internet will be is the power to discriminate in content and services. The aim of this form of Internet access will not be openness and neutral platforms; the aim of this form of Internet access will be control over the content that gets played.” (Lessig, 2002: p. 184)
According Lessig the providers will insist that it is their right to layer onto the application layer of the Internet. In the end, the possibility for the providers to filter the application layer is made possible by the organizational structure of the network. For the application layer is nested into on all previous layers, in the end resulting in all layers to be dependent on the link layer –the layer that is now being controlled by the providers.
This means the discrimination of protocols such as VoIP is made technically possible, but Lessig stresses out the consequences: When providers discriminate data this will be at the expense of the open feature of the Internet commons. Resulting in drastic consequences for innovation (Lessig 184).
Concluding
And it is exactly innovation that threatens the telecom industry. Its decline of profit is mostly caused by innovative products that are based on the open features of the Internet. In our case study, threatened services like Skype or WhatsApp are part of a new industry that is colliding with the established industry. From this perspective, it is interesting to know that Google, being perhaps the biggest representative of this new industry, together with Amazon and Microsoft is promoting for a law that guarantees net neutrality (Hahn and Scott 3). The new industry is built around a neutral platform, protected by its protocols.
As Lessig states, the protocols that govern a network are not fixed, they can be replaced by different protocols later on. There is nothing that forces obedience to the neutrality of the net. The Internet is merely a set of protocols that is free to be supplemented with protocols added on top. Any one is free to change it (Lessig 183). In our case, this is what the mobile providers want to do: to alter their protocols at the link layer to discriminate data from the application layer, making use of the protocols itself to discriminate.
Bibliography
- Extensible Messaging and Presence Protocol (XMPP): Core. n.d. XMPP.org. 15 October 2011. <http://xmpp.org/rfcs/rfc6120.html>
- Deleuze, Gilles. “Postscript on Societies of Control.” October Vol. 59, (Winter 1992) 3-7
- De nieuwe strategie van 2015. n.d. KPN. 01 October 2011 <http://www.kpn.com/web/file?uuid=c310519a-9940-494b-90d9-f7bdf39509fc&owner=274f122e-3673-4808-9c80-2d2871a9604d>
- Federal Communications Commission: Voice-Over-Internet Protocol. 2010. FCC.gov. 27 October 2011 <http://transition.fcc.gov/voip/>
- Galloway, Alexander R. and Thacker, Eugene. “Protocol, Control and Networks.” Grey Room 17, (2004). 6-27.
- Galloway, Alexander R. “Physical Media.” Protocol: How Control Exists after Decentralization: Cambridge, MA: MIT Press, 2004. 29-53.
- Haes, Andraes Udo. “Europarlement hamert op Netneutraliteit” Webwereld.nl 22 October 2011 <http://webwereld.nl/nieuws/108327/europarlement-hamert-op-netneutraliteit.html>
- Hahn, Robert and Walson, Scott. “The economics of net neutrality.” The Economists’ Voice. 2006. Bepress.com. KPNs nieuwe strategie internet diensten is apart betalen. Bits of Freedom. 2010. 10 May 2011 <https://www.bof.nl/2011/05/10/kpns-nieuwe-strategie-internetdiensten-apart-betalen/>
- Lessig, Lawrence.. “The Architecture of Innovation” Duke Law Journal. 51, (2002) 177-191
- Network neutrality resolution amendments. n.d. La Quadrature du Net. 15 October 2011 <https://laquadrature.net/wiki/Network_Neutrality_resolution_amendments>