[Research] Trade Your Location Information For Security?
A Liberty-Security Tradeoff in Public Policy for the Location Information Technology in South Korea
This afternoon, you might tag where you have been for lunch on facebook, or even a few minutes ago, your smartphone might update you with new emails. Information and Communication Technology(ICT) already became pervasive to our daily life, pervasive enough to threaten individual information unknowingly in the huge data network. So, ICT policy has been concerning how to govern the data system. As such, our society surely institutionalized dataveillance, the term coined by Clarke in 1988 (1). What is observed at the center of dataveillance is the double nature of ICT. It enables us to participate in society through wider, readily accessible network of information, but at the same time, it seems to violate our rights by exposing our individual information. Thus, it especially invokes sharp conflicts between liberty and security.
In particular, location information technologies deepen this conflict, as allowing personal location to be exposed and tracked on the real-time basis. And due to their double nature, the relevant public policy has a difficulty in planning, goal setting, and implementation. Its main homework should be to handle the clash between two policy criteria: liberty and security. In order to study location information as a new type of personal data as well as its relationship to surveillance, I analyzed how the public and government perceive this technology and how that perception is reflected to public policy in practice with a content analysis of the recent debates on the legislation of regulations on location-based services (LBS) in South Korea.
The analytical framework draws on the conflicts inherent in multiple goals of public policymaking, so called a tradeoff. There are major 4 goals in public policy-liberty, security, efficiency and equity. They deeply affect policy formation, implementation, and evaluation, so that they are used as criteria in justifying and evaluating policy (2). Unfortunately, it becomes problematic to interpret each criterion. For example, let’s define liberty as ‘do as you wish as long as you do not harm others’ in line with Mill’s idea. Once we try to apply this criterion in policy analysis, it becomes ambiguous to interpret ‘harm others.’ To what extent can your behaviors be regarded as not harming others? More fundamentally, what would you classify into ‘harms’? Due to these tricky interpretations, these policy criteria are often in conflict. Besides, it is also ambiguous to decide when one criterion should be overruled by another. So, when examining a trade off in policy analysis, we should pay attention to the actual degree of tradeoff.
Based on the content analysis of first-hand materials published between 2002 and 2009 classified along the four dimensions (individual vs. public security, positive vs. negative liberty), the following study results demonstrate a significant divergence between the public and governmental understanding of the liberty-security dilemma of LBS. (3)
[Figure 1]
[Figure 2]
[Table 1]
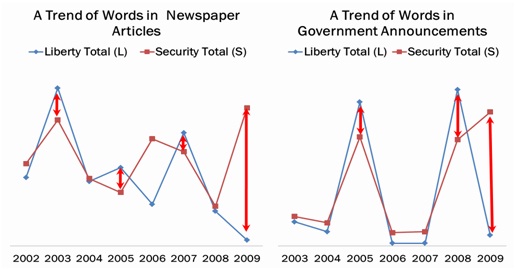
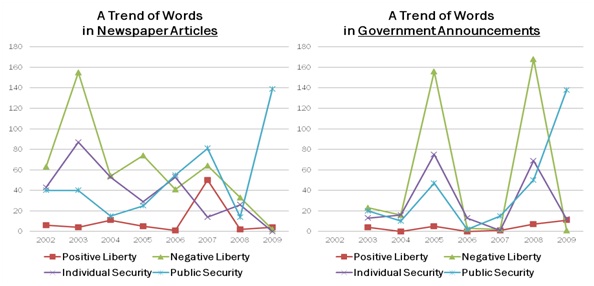
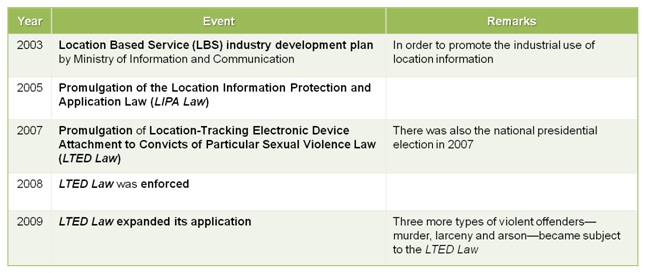
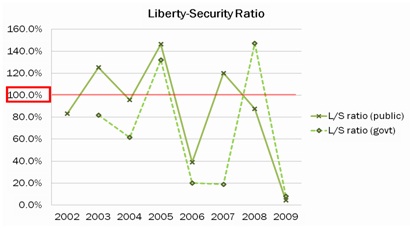
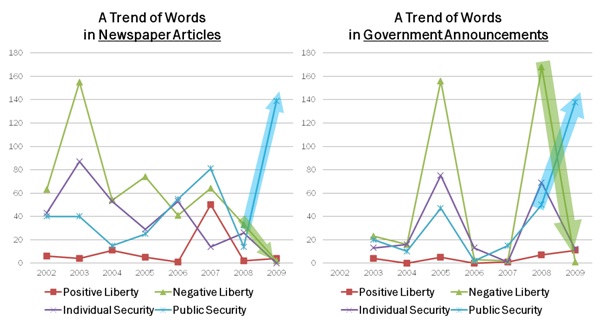
The years of location-information-related major events (refer to Table 1) observe noticeable differences among word counts of each coding category (Figure 2) as well as total counts of liberty side and security side (Figure 1). Thus, both the government and the public have responded and acted based on a firm belief in liberty-security tradeoff in location information technology.
[Figure 3]
The ratio of security to liberty is always a bit higher on the public side than the government side (Figure 3). It shows that the public is more sensitive to technology’s impacts on liberty, that is, whether liberty is invaded for security.
Especially, the public shows a continuous emphasis on negative liberty regardless of issue saliency (Figure 2). This indicates that the public basically perceive location information technology as invasive to their liberty and understand it in aspect of privacy issue. Thus they perceive location information and its social consequences as violating their fundamental rights, much more than setting boundary to their behavior.
The government reflected this public perception to makes a decision on public policy and law about location information technology, as clearly observed in the promulgation of the LIPA Law in 2005 and enforcement of the LTED Law in 2008. While the government reflected the public’s underlying perception, the government basically stresses both individual and public security regardless of issue saliency.
[Figure 4]
Meanwhile, when the goal of improving public security is explicitly addressed, both the public and the government are much less sensitive to tradeoff. It is evidenced by a trend of word counts during the period from 2007-2009 when a couple of events relevant to the LTED Law happened. Notably, from 2008 to 2009, both sides show the drastic increase in pubilc security and decrease in liberty as the LTED Law was questioned to expand its application (Figure 4). More convicts subject to location tracking devices, thus under control. So, as the strong purpose of improving public security is dressed directly, they are apt to easily trade liberty to security, even the public who are very sensitive to liberty being traded.
To sum up, the public’s continuous, extra emphasis on negative liberty suggests that they fundamentally perceive location information technology as invasive to their liberty, basic rights. Thus, they are likely to understand this technology in relation to privacy issues. And the government, while reflecting this public perception, it stresses security continuously in a way of protecting privacy. However, when the goal of improving public security is overtly addressed, both the public and the government are apt to easily trade liberty to security as shown in the LTED Law case.
While responding to the public perception, the government approaches governing location information not as matter of reducing surveillance but as matter of protecting privacy. Expanding the application of LTED Law in 2009 well illustrates this aspect. It implies that the relevant policy and law can easily blind the public to alarming at which point surveillance becomes excessive. Compared to when LTED Law was enforced in 2008, in 2009 both the public and the government showed the intensified tendency of pursuing public security as more willingly accepting the possibility of ‘privacy’ infringement. The issue was hardly worried from the perspective of the expanding scope of surveillance, but only justified from the perspective of improving security based on a belief in liberty-security tradeoff. This plausible justification of improving security can make the public insensitive to over-surveillance. Also, it can be only nominal justification in order to propel commercial interests, law enforcement and social control objectives (4).
This way of legal/policy response evidenced in Korean case fails to politicize the problem of excessive surveillance. If this tendency continues, both the public and the government will be under the illusion by manipulating ‘security’ purpose with ever-more enhancing location information technology. Then, both become insensitive to recognize excessive surveillance so that the government unknowingly adopts invasive and authoritarian way of dataveillance. Therefore, we need discuss privacy protection and dataveillance in the political domain more actively and openly.
(1) Clarke (1988) Information Technology and Dataveillance. Commun. ACM 31.5: 498-512.
(2) Stone (1997) Policy Paradox: The Art of Political Decision Making. New York: W. W. Norton & Company.
(3) The data include announcements from government and governmental agencies (from Korea Policy Portal website) and news articles (from 4 major news papers in Korea).
(4) Kirby C. (2000) New Technology Can Pinpoint Cell-Phone Users’ Locations. San Francisco Chronicle, 23 October 2000.