Facebook in the Spotlight of the Dark Web
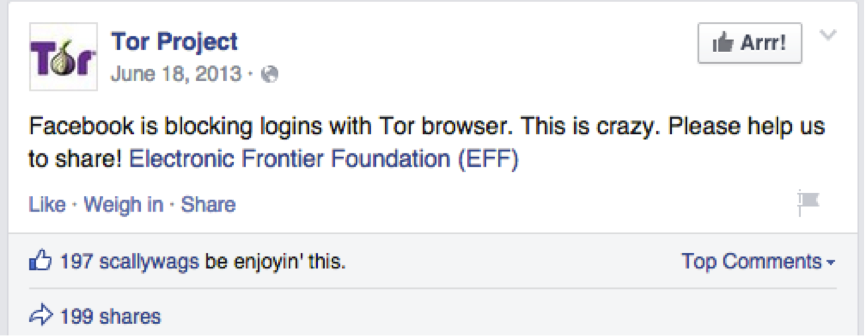
“Facebook is blocking logins with Tor browser. This is crazy. Please help us to share!“ (Facebook, 2013) published Tor Project on Facebook on June 18th 2013. This is not the case anymore. Facebook opened a service for all users that want to stay anonymous via Tor software. A safe connection to one of the world’s biggest web pages was established in the URL https://facebookcorewwwi.onion/.
Facebook reviled this option on October 31st on their subpage Protect the Graph that informs you, as they put; ‘…about securing Facebook and the web’. Alec Muffett, who works as a Software Engineer for Security Infrastructure at Facebook London explains in his post: “It’s important to us at Facebook to provide methods for people to use our site securely” (Facebook, 2014). Nevertheless there was no announcement about this matter on the official Facebook Newsroom.
Accessing Facebook via Tor encrypted network is kind of a contradiction, where Facebook exists as a service based on collecting user data, and Tor as a service that protects the data at all costs. As introduced, in the past Tor users encountered numerous problems with accessing Facebook, however, the darkest scenario where Facebook would block connections from Tor browsers was not true, as was explained on Tor blog later on 18th of June 2013.
“A number of users have noticed that Facebook is blocking connections from the Tor network. Facebook is not blocking Tor deliberately. However, a high volume of malicious activity across Tor exit nodes triggered Facebook’s site integrity systems which are designed to protect people who use the service. Tor and Facebook are working together to find a resolution.” (The Tor Blog, 2013)
Regardless resolving the issue, no major breakthrough has been made. All that Tor and Facebook managed to do, was to restore the routes between them, but still only over the standardised protocol.
The introduction of the Facebook Onion Address on October 31st provides Tor users to connect to Facebook’s Core WWW Infrastructure, as Muffett explains in the blog post, “it provides end-to-end communication, from your browser directly into a Facebook datacentre” (Facebook, 2014).
A Tor network promise to its users is that Tor “…provides an anonymity layer for TCP by carefully constructing a three-hop path, or circuit, through the network of Tor routers using a layered encryption…” (McCoy, 2008). This gives users anonymity when browsing and helps them to keep their personal information to themselves.
In the Facebook case it is not like that, anonymity on the web page is not an option, users only gain another layer of security on the top. As one of the former Tor developers, Runa Sandvik, explains for Wired: “No, you’re not anonymous to Facebook when you log in, but this provides a huge benefit for users who want security and privacy” (Wired, 2014).
Also on Tor blog one of the developers by the nickname arma, concurs with the Facebook’s decision of making an onion address, however, Facebook still gathers user information. Its main advantage of Facebook’s onion address is that it allows users to access Facebook from the places they otherwise could not.
“…Iran blocked Facebook, a good chunk of the Persian Facebook population switched over to reaching Facebook via Tor/…/. Other countries like China followed a similar pattern after that.” (The Tor Blog, 2014)
He also supports the decision because it can make an impact on other web sites to adopt an onion address and help to spread the world of the secure connections. “So I am excited that this move by Facebook will help to continue opening people’s minds about why they might want to offer a hidden service, and help other people think of further novel uses for hidden services.” (The Tor Blog, 2014)
Facebook’s decision was accompanied with a great number of satisfied users, but some of them are also in doubts about the intentions of Facebook’s hidden service.
Suna Sandvik also stated for Wired that “You get around the censorship and local adversarial surveillance,”(Wired, 2014). A research of connecting to Facebook via onion address showed us a bit different results than expected. Using Tor browser and Facebook onion address still provided us with advertisements based on our current location. Some might say the reason for that is our place of residence, but also by trying to change it, Facebook continues to offer us ‘right’ advertisements.
Despite all the suspicions, users who care about their online safety and privacy of personal data gained a major breakthrough.
References:
“Facebook: Making Connections to Facebook More Secure.” N.p., n.d. Web. 5 Nov. 2014.
“Facebook: Tor Project – Facebook Is Blocking Logins with Tor Browser. This…” N.p., n.d. Web. 5 Nov. 2014.
McCoy, Damon et al. “Shining Light in Dark Places: Understanding the Tor Network.” Privacy Enhancing Technologies. Ed. Nikita Borisov and Ian Goldberg. Springer Berlin Heidelberg, 2008. 63–76. link.springer.com. Web. 5 Nov. 2014. Lecture Notes in Computer Science 5134.
“The Tor Blog: Facebook and Tor.” N.p., n.d. Web. 5 Nov. 2014.
“The Tor Blog: Facebook, Hidden Services, and Https Certs.” N.p., n.d. Web. 6 Nov. 2014.
“Wired: Why Facebook Just Launched Its Own ‘Dark Web’ Site.” N.p., n.d. Web. 6 Nov. 2014.