Anti-social apps: counterattacking the power of networks
We judge ourselves with the means other people have and have given us for judging ourselves. Into whatever I say about myself someone else’s judgement always enters. (Jean-Paul Sartre)
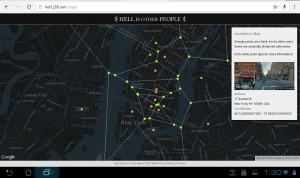
In 2013, Scott Garner, an artist based in New York, created and launched a web application called Hell is Other People. Garner’s application – named after a well-known quote from Jean Paul Sartre’s No Exit (Huis Clos) – allows users to monitor their “friends” and “calculate optimally distanced locations for avoiding them”.
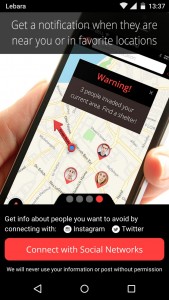
This milestone in the world of anti-social media did not represent just an isolated episode. In fact, one year later, two (anti-social) mobile apps called Cloak (iOS) and Time to Split (iOS/Android), respectively, were released. Needless to say, these apps aim to help users to elude their social media “friends” in everyday life. Cloak development stopped in October 2014, so that Time to Split is apparently the most up to date and functional anti-social app around.
However, that does not mean that Time to Split has no issues. First, according to several sources (Perez 2014; Lee 2014) it can be connected to Facebook, Instagram, Twitter and Foursquare. But it actually supports just Instagram and Twitter on Android systems. In the second place, it is obviously not possible to avoid “friends” who have not logged in. And Finally, it seems that, apart from a great initial interest by tech and mainstream press, anti-social applications struggle to take hold.
It is interesting to note, that, despite their low popularity, apps like Time to Split pose unsolved questions about the relationship between our “online” and “offline” status.
Over the last years, social media platforms have risen “from niche phenomenon to mass adoption” (Acquisti and Gross 2005; Raynes-Goldie 2011) and it is therefore complicated to understand the small gap between the private and public sphere of people. We might also argue that there is a strange sense of safety (Bigge 2006) in online networking, and sometimes social media users tend to classify their social counterparts depending on their status (online, abstract; offline, concrete).
At the same time, there is an emerging network power which operates both inside (cf. Castells 2011) and outside the Internet. This force should be interpreted as a form of coercion (cf. Foucault 1982) – explicit or not – which activates constraints and mechanisms within a domain of relationships. Even though we decide not to take part in the “game of media”, we are destined to be mediated by network narrations and their actors. Take, for example, someone who tags you on Facebook even though you are not there. In a certain way, we have to be part of this mediation in order to exist socially and culturally.
Hence, I believe it is extremely interesting and useful to exploit social media to do something which they are not supposed to do. In my opinion, an increasingly number of people, who are on social media platforms, cannot avoid their online presence. At the same time, they are probably aware that their presence is due to a constraint created by the network itself. Anti-social applications such as Time to Split try to mark new spaces and distances against a standardization of social environments (van Dijk 2006). They challenge the contradiction of friends, followers, contacts: people who are supposed to play an “important” role in our online life but not in that offline one. And that action is somehow an overturning of a coercive mechanism. Michel Foucault might have probably called this move a case of counterattack. In fact, unlike violence, power is “always a way of acting upon an acting subject or acting subjects by virtue of their acting or being capable of action” (Foucault 1982, 789).
Using social media as a counterattack tool should make us aware of the mediated sociality mechanism. We are actually always mediated through the others. Therefore, the real issue is that of trying to understand how we are mediated by other people, and what is the narration which comes out of this process. Ultimately, we should try to understand how the power of networks seizes our relationship. And – no, there is no specific app to avoid that.
References
Bigge, Ryan. “The Cost of (anti-) Social Networks: Identity, Agency and Neo-Luddites.” First Monday 11.12 (2006).
Castells, Manuel. “Network Theory | A Network Theory of Power.” International Journal of Communication 5 (2011).
Foucault, Michel. “The Subject and Power.” Critical inquiry (1982).
Garner, Scott. “Hell Is Other People.” http://hell.j38.net/.
Gross, Ralph, and Alessandro Acquisti. “Information Revelation and Privacy in Online Social Networks.” Proceedings of the 2005 ACM Workshop on Privacy in the Electronic Society. 2005.
Lee, Tyler. “Split App Uses Location Data To Help You Avoid Certain People.” Ubergizmo. 2014.
Perez, Sarah. “Chris Burch & Others Put $1 Million Into Split, An App For Avoiding Your Exes And Others You Don’t Want To See.” TechCrunch. 2014.
Raynes-Goldie, Kate. “Aliases, Creeping, and Wall Cleaning: Understanding Privacy in the Age of Facebook.” First Monday 15.1 (2010).
van Dijk, Jan. The Network Society: Social Aspects of New Media. 2nd ed. Thousand Oaks, CA: Sage Publications, 2006.