World Wide Web Consortium and Digital Rights Management: Innovating Stagnation

Artistic illustration of DRM, as seen on the EFF website.
The history of “Digital Rights Management” software while relatively new, has been quite controversial. Oftentimes advocates of online privacy and security argue about the possibilities of abuse stemming from such DRM technologies, along with activists and proponents of the “open source” initiatives. These supporters of openness are constantly trading blows with advocates of corporate ownership and copyright protection. Both of these sides seem to have valid reasons for their arguments, however after a closer inspection one can easily distinguish the underlying motivations of the two groups and make a decision as to who might be in the right.
What Is DRM?
Digital Rights Management (DRM), “is a collective term for tools whose purpose is to enable owners of copyright works to control their use” (Clarke 1), additionally Mulholland (3) describes DRM as a series of systems that are deployed in order to protect Intellectual Property. This Is were the first counter argument is found, generally in the works of open(free) software researchers and activists. Richard Stallman on the other side argues that DRM is not used to “manage rights” but to restrict them (88). Seeing things from the side of the consumer he argues that DRM should be in fact called “Digital Restrictions Management”, since it is restricting the users control over their machines and their content while also providing countless opportunities for abuse by corporations and lawmakers (Stallman 131).
What is EME?
As of 18th of September 2017 the World Wide Web Consortium, better known as “W3C”, has officially released “Encrypted Media Extensions” (EME) as a standard recommendation, thus effectively standardizing the creation of browser extensions that could be used control access to specific forms of media. However, there are certain well structured and long standing arguments against the implementation of such technologies, especially when it comes to their use as web browser plug-ins.
What is the W3C?
The world Wide Web Consortium (W3C) according the their website is “an international community where Member organizations, a full-time staff, and the public work together to develop Web standards”. Standards like the current HTML 5 are used in the creation of most, if not all current websites and were created by the W3C and their collaborators. In the case of the “Encrypted Media Extensions” (EME), the research and creation of the web standard was spearheaded by corporations like Microsoft, Google and Netflixi (According to the official document released by the W3C detailing the research and creation of the proposed EME the necessary work was conducted by David Dorwin from Google Inc. Jerry Smith from Microsoft Corporation, Mark Watson from Netflix Inc and Adrian Bateman from Microsoft Corporation), with this initiative beginning back in 2013. Consequently the fact that the current EME standard was created by representatives from the aforementioned corporations testifies as a good example of corporate control over the current DRM rhetoric within W3C. Indeed Clarke (3) seems to have predicted the permeation of corporate interests into the main body of W3C back in 2001. Clarke claimed that the current political trajectory of “economic rationalism” could lead to corporations actively trying to “subjugate consumers” (3).
What are some of the main arguments surrounding the standardization of EME?
Specifically W3C argues in their description of EME about the levels of security and privacy that this API can give to users:
“The EME specification has been developed with a focus on the security and privacy of the user. Compared to previous methods of viewing encrypted video on the Web, EME has the benefit that all interactions happen within the browser. EME moves the responsibility for interaction with encrypted video from plugins to the browser, which acts as a true user agent”, (Le Hégaret 1)
On the opposite site of the argument Cory Doctorow, of the Electronic Frontier Foundation, in an open letter directed at the members of the W3C argues that EME act with the exact opposite function. In fact he argues that EME is a danger to both the privacy and the security of the user. Doctorow argues that, “those very benefits (such as improvements to accessibility and privacy) depend on the public being able to exercise rights they lose under DRM law — which meant that without the compromise the Director was overriding, none of those benefits could be realized, either”. He also argues that by not including any protection against security specialists breaking the DRM in order to discover security issues, EME becomes less secure, since every attempt to break their code (ever for security research) is now illegal. In addition to that, according to the EME specifications there is no provision protecting security researchers cracking and accessing the application’s code for security reasons (Doctorow). Therefore any attempt by specialists to identify potential vulnerabilities within the plugins is deemed as illegal. This opens a potential “Pandora’s box” for exploitation of the various vulnerabilities that unavoidably come with every new technology.
In addition to the current discussion surrounding the very recent creation (suggested in 2013 standardized in 2017) of EME by the W3C, there have been several other arguments against the creation and implementation of DRM systems in general. To fully gasp the significance of the recent events, one must take a look at the political, social and economic context that surrounds the creation of such systems.
Adding to Doctorow’s critique against DRM systems are the various privacy and security issues arising from the use of such technologies. For example Poorvi, Reynolds, and Dickinson underline the many ethical and political issues originating from the extensive recording and profiling of personal information that DRM technologies require in order to function, as well as the various issues stemming from the accumulation of such information by corporate interest groups(1). One example of the dangers hidden behind this massive accumulation of personally identifiable information are the recent Equifax leaks that had the personal information of millions leaked on the web, thus underlining the corporate responsibility issuing from such occurrences.
When it comes to social and ethical issues W3C failed to consider accessibility workers trying to provide access to people with disabilities trying to use EME. Therefore, any attempt to modify the DRM systems in order to provide access to people with disabilities is now illegal (since every attempt to modify the system is not permitted) according to the new standard. However, the need to consider placing safeguards for people with disabilities has been a long standing proposal according to an article by Yun and Tan written back in 2012. They argue about the need to include Visually Impared people in all considerations surrounding the creation and implementation of DRM standards. As it can be seen in the final version of the EME document from W3C, this was not the case. Even despite initial arguments from members such as the EFF, the final version of EME disregards any and all arguments about the rights of accessibility specialists to developing and using the standard in order to provide access to people with disabilities.
Furthermore, Gupta argues about the lack of representation of non western world actors in process of web standard creation (1). As Gupta describes, within the main body of W3C, there is a serious lack of representatives of non western countries, as well as a lack of females and members of minorities(1). This observation significantly undermines the validity of many controversial decisions the W3C has made , including the standardization of the EME, since the decision was taken by a majority of representatives from western corporate interest groups.
Taking a look at the technical issues:
After a closer look on the technical structure of the new EME technologies some important issues arise. According to Simmons and Arbanowski, “EME enables a JavaScript application to select a content protect mechanism and facilitate key acquisition”(3).
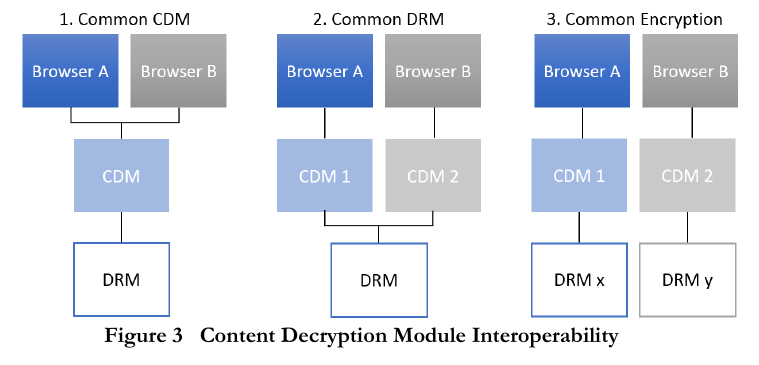
Illustration of the decryption module plugins within the browsers as illustrated by Simmons, John and Arbanowski (3).
Essentially in order for EME to properly function within modern browsers there needs to be a backbone of JavaScript plugins to support EME within the browsers environment. The extensive use of JavaScript applications significantly decreases the security of the browser. Guarnieri and Salvatore in their research conducted in 2011 concerning JavaScript vulnerabilities identify 526 vulnerabilities in 11 sites that use JavaScript (177). Additionally Bielova in a survey about “JavaScript security policies and their enforcement mechanisms in a web browser”, describes how by inserting malicious JavaScript code into a web application attackers can can gain the same privileges the original code possessed (243). This is especially worrying when it comes to EME plugins, since their inherent DRM capabilities require deep access to both the network and the computer of the user along with the web browser application. Therefore by compromising the installed EME an attacker could gain underrepresented access to the user’s personal data (used for identification purposes by the DRM software), thus creating huge privacy and security issues for the user (Bielova 243).
Conclusion, innovating stagnation:
By concluding this short argument, one must wonder how an organization like the W3C created for fair and equal access, or better put a “web for all” and a “web for everything” (as it can be seen in the about section of their website) could work to create and standardize EME, a technology built to restrict access and innovation. In essence DRM systems are created to restrict and control access to the users, while also giving unprecedented power (and the ability to abuse said power) to the already extremely powerful media corporations (Stallman 131).
The future of W3C and DRM technologies:
Finally, there seems to be a continuous tendency for increased corporate control over both the technical and the political infrastructure of the web. Moreover, this recent development within the W3C indicates the deep roots corporate interests have within the most important organizations and structures of the INTERNET. As it has always been the case, corporations do not care for the consumer or in this case the user, their only drive is more profits and subsequently more control over their products (in this case via DRM technologies). If this trend continues unobstructed we may very soon find ourselves battling for the right to control our computers and our online lives.
Literature:
Bielova, Nataliia. “Survey on JavaScript security policies and their enforcement mechanisms in a web browser.” The Journal of Logic and Algebraic Programming 82.8 (2013): 243-262.
Doctorow, Cory. Content: selected essays on technology, creativity, copyright, and the future of the future. San Francisco: Tachyon Publications, 2008.
Doctorow, Cory, et al. “Digital Rights Management (DRM): a failure in the developed world, a danger to the developing world. A paper for the International Telecommunications Union, ITU-R Working Party 6M Report on Content Protection Technologies.” (2005): 1-28.
Gupta, Harsh. “(Lack Of) Representation of Non Western World in process of creation of Web standards.” arXiv preprint arXiv:1609.01996 (2016).
Guarnieri, Salvatore, et al. “Saving the world wide web from vulnerable JavaScript.” Proceedings of the 2011 International Symposium on Software Testing and Analysis. ACM, 2011.
Mulholland, Judie. “Digital Rights (mis) Management.” W3C DRM Workshop. 2001.
Simmons, John C., and D. S. Arbanowski. “Interoperability, Digital Rights Management and the Web.” (2013).
Stallman, Richard. Free software, free society: Selected essays of Richard M. Stallman. Lulu. com, 2002.
Vora, Poorvi, Dave Reynolds, and Ian Dickinson. “Privacy and digital rights management.” A position paper for the W3C Workshop on Digital Rights Management. Publishing Systems and Solutions Lab., Hewlett-Packard Laboratories, 2001.
Yun, Corinne Tan Hui. “Moving towards a More Inclusive Copyright Regime for the Visually Impaired.” Singapore Academy of Law Journal 24.2 (2012): 433-469.