Make voting safe again? A selection and as-sessment of contemporary technologies in relation to their integration with i-Voting
By conducting an academic literature review along with an empirical analysis of the Estonian i-Voting system, our aim was to identify weaknesses in the i-Voting infrastructure, and assess whether biometric technologies can be implemented to help alleviate issues and construct a secure online democratic process.
Project Idea
Whether analog or digital, any healthy democracy needs a secure infrastructural base to afford citizens the opportunity to vote. By analysing contemporary i-Voting infrastructures through an empirical analysis of the Estonian local government election of 2017, and cross-referencing this with the historic use of both e-Voting and i-Voting, along with pertinent security debates in academic literature, we aimed to critically assess whether biometric technologies could advance what has been, until now, slow adoption of computerised democracy. The biometric systems chosen for analysis were face recognition and fingerprint identification technologies.
Context
After the controversial Catalonian referendum of 2017 (BBC n. pag.) and violence on Election Day in Ukraine in 2014 (Oliphant n. pag.), our team realised that democracy has always been intimately tied to physicality, and the politics of the spatial. Both events inspired our team to consider taking the physicality out of democracy, and what implications this might have. Turning to developments in the technology, we highlighted a growing trend and affordability of biometrics. Founded in 2003, the European Biometrics Forum was set up to specifically discuss the intricacies of biometrics. After assessing several technologies capabilities, we narrowed our focus to fingerprint scanning and face recognition software and the possibilities this could add an additional layer of security to i-Voting.
To contextualise our project, we first turned to discussions in the mainstream media about i-Voting. Estonia is currently the only EU country that has adopted i-Voting during major elections, with Durumeric et al. claiming that “more than 30% of its ballots cast online” (702). By broadening and deepening the research scope, it revealed a seemingly unending flow of complex security and privacy processes that must be negotiated. Many channels of vulnerability were identified, such as attacks that “depend on fundamental vulnerabilities in the current PC architecture (malicious code, for example) and in the Internet (such as spoofing and denial-of-service attacks)” (Jefferson et al. 64).
Relevance
Initially, we identified that the three major obstacles for the widespread adoption of i-Voting, attempting to assess biometric technology’s impact on each:
- Networked, internet-based infrastructure presents huge security concerns as opposed to e-Voting. Afforded the right circumstances, attackers could have the possibility to change votes, cast ballots, and even access voters’ identities. Internet voting is much more easily hackable than the actual voting machines (Sharma et al. 46).
- Present i-Voting systems are time consuming and require manual verification of the voter’s identity through the use of passwords and other mechanisms (Sharma et al. 46).
- The server infrastructures need huge and secure storage capacities, and the initial cost of purchasing this is expensive (Sharma et al. 46)
Methodology
After the initial mainstream media analysis, we first conducted a thorough literature review with regards to the historic processes of electronic voting. Following this, we examined the development, strengths and weaknesses of contemporary biometric technologies. This was focused around security infrastructure, voting processes and the implementation of biometrical systems. Once completed, we moved towards a critical assessment of the academic literature and debates concerning the implementation of i-Voting.
During our analysis, we primarily focused on user-side risks because of the relative opacity of server-side issues. However, we did map the digital vote’s path through server-side infrastructure to identify potential risks.
With this in mind, we critically investigated the involvement of i-Voting in the Estonian Local Government Elections of October 2017 and explored user-side technical protocols in place, and cross-referenced this with the security risks we had identified. To visualise these results, we revised the interface of the recent Estonian Local Government Elections by modifying screenshots with the implementation of biometric systems to identify the voter.
Biometrics in the i-Voting process
In light of time and content restrictions, unfortunately not all possible biometric technologies could be assessed. We singled out the two most feasible: face recognition and fingerprint recognition, were chosen.
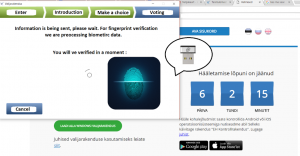
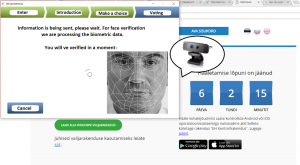
Visualization of how the Estonian I-Voting system would incorporate the biometric verification systems
1. Fingerprint verification
2. Face recognition
When considering implementing biometric data, we noted some of the identified disadvantages could be circumvented. According to Jain et al., possible advantages would include streamlining server infrastructure (and therefore cost), rapid verification, an extra layer of identity protection, and ease of democratic participation when compared with cryptographic keys, as biometric data cannot be lost or misplaced (92).
However, according to Stroup there are several negative sides when using biometric verification (“Use High-Tech Personal Security To Keep Your Information Safe,” n.pag.). For example, the sheer invasiveness of harnessing biometric property, the vulnerability of biometric data on data servers, the expensive initial implementation cost, the irreplaceability of biometric property once compromised and a potential lack of accuracy, leading in the worst case to system failure (n.pag).
To utilise facial recognition, every user has to have a specifically figured, high-definition camera (Adesua 22). The voter’s face is scanned and a digitised face mask is cross-referenced with a purpose-built database (22). Several problems are apparent with this method. Even the growth of facial hair can skew the reliability of such a system, leading to a great number of verification problems and thus driving up administrative costs as election employees scramble to verify voter’s identity.
A finger verification system, on the other hand, can be connected to any computer through using a small USB fingerprint reader and can read unchanging biometric data with great accuracy. In the case of bodily modification, however, the reader will be unsuccessful. Furthermore, biometric data does not prevent identity attacks once this data has been digitised. We must conceive of digitised fingerprint data, once it has left the user, fingerprints as codes, encrypted like password identifications and just as open to attack (Jain et al. 55).
Using biometric systems, it’s almost impossible to get totally error-free results. For example, differences in the environment during the data collection (lighting, temperature, etc.) and the differences in equipment used (cameras, scanning devices, etc.) are big issues and impossible to impose adequate levels of standardisation upon. The most commonly used standard performance evaluation criteria are the False Accept Rate and the False Reject Rate, which have the advantage of being customisable to the system you are using (Stroup, “Biometric Identification and Identity Theft,” n.pag.)
Taking into account the increasing standardization of biometric technologies for interoperability, it is generally accepted that the centralized storage of biometric data increases both the risk of using biometric data as the key to interconnecting many databases (which may lead to the creation of a detailed profile for an individual), as well as risks associated with the reuse of such data for insidious purposes such as unauthorized access (Natgunanathan et al. 881).
Anonymity of i-Voting
A central pillar of democracy is the guarantee of a secret ballot in order to protect their voting preference from public access. In traditional forms of voting, the voter casts their ballot inside a physically and visually secure location such as an opaque ballot box in a protected zone. Electronic processes pose fresh and daunting challenges for the separation of voter and vote (Abdullah et al. 2).
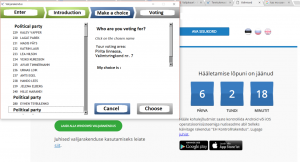
[To start I-voting in the Estonian system, one must download a client application, which is available for download for free on the state website. The source code is published in advance. After installing the client, a voter connects through their personalized smart ID card. Next, the voter runs the application and the current system asks for the 4 digit pin and connects to the election server, authenticating via a transport layer of security. ]
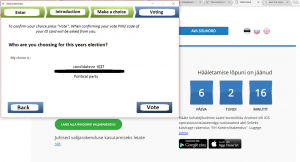
[After, the system geographically locates the user, and the user casts their vote. A new application system is created for each election (Halderman, 00:25:26-00:27:22). ]
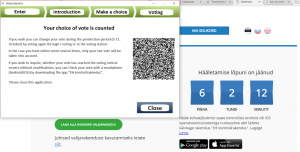
[Once the vote has been cast, the ballot choices are encrypted and cryptographically signed using the voter’s national ID card. The signature is attached to the vote is uploaded to the electoral servers until counting takes place. Finally, a screen displays a feature for verification with a QR code (Halderman, 00:27:22-00:28:22). ]
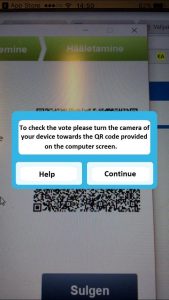
[The QR code contains a ballot ID along with random coins that were used to pad the vote (secure the vote) (00:27:22-00:28:22). The voter can scan the code with a smartphone, and in turn the app sends a ballot result without the signature. This validation procedure can be done only 3 times and up to 30 seconds. The voter has the ability to replace their vote as many times as they wish, with only the most recent vote counted.]
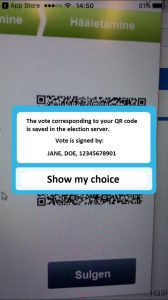
[When counting begins, the cryptographic signature can be imagined as an inner envelope with the ballot and an outer envelope with a name and signature in a digital form (Halderman, 00:28:26-00:30:42). To count the votes, the inner and outer signatures are separated and shuffled. Signatures are stripped off and burnt onto a DVD, before being deleted (00:30:26-00:31:40). Next, the counting server that has access to the private key is used to encrypt the ballot (00:31:40-00:32:39). The counting server never comes into contact with the signatures, and the counted votes are formatted into the election results. ]
To separate voter identity from casted ballot, the Estonian voting system uses public key cryptography. The cryptographic technique involves a ‘double envelope’ whereby a digital signature used to identify the voter functions as an outer envelope, while public key encryption functions as the inner envelope to protect the ballot. After establishing the voter’s eligibility, the outer envelope is removed and the anonymous encrypted ballots can be stored and counted (Durumeric et al. 705). However, some researchers have criticised the security and transparency of this use of complicated procedural controls (703). Other strategies to ensure the voter’s anonymity with the use of cryptographic methods are being developed in academic literature (Kawabe et al. n. pag.; Heather et al. n. pag.).
Literature Review
The academic debate surrounding the possibilities and pitfalls of i-Voting can be roughly divided into two periods: one beginning in the late 90s and ending around 2008/9, and one from 2009 onwards. These debates revolve almost exclusively around either issues of security or of privacy.
The first period was characterised by extreme scepticism and uncertainty. Although Estonia launched its i-Voting system back in the early 2000s, this period also witnessed growing scepticism around the promises of the internet, with events like the dotcom crash and intense ethical and legal debates surrounding online piracy.
In 2000, the Californian Secretary of State commissioned a task force to investigate internet voting. He identified that ‘one of the most difficult tasks for an Internet voting system is the authentication of voters’ (Jones 1). The following year, MIT and Caltech conducted a joint study into i-Voting. They concluded that i-Voting was indeed the only way to feasibly advance democracy, but highlighted the exorbitant costs in implementing the new system, particularly the risk of a DDOS (Denial of Service) attack (Alvarez et al. 28). In the same year, the American National Commission of Federal Election Reform concluded that i-Voting was ‘an idea whose time most certainly has not come’ (NCFER 44).
After 2009 however, as the world began to crawl its way out of the financial crisis, the sentiment towards i-Voting changed noticeably. Estonia’s i-Voting system had been ticking over without any major dramas, Norway launched its pilot project in 2013 (Carter Centre, n.pag.) and technological advancements, such as advances in cryptography, the explosion of the open-source culture, the invention of blockchain technology and the increasing affordability of biometric devices injected fresh optimism into the idea.
By conducting a basic operational security analysis, we were able to divide both privacy and security risks on an infrastructural level, as either client-side or server-side compromises.
Regarding security issues, there are two main areas of concern for the security of internet voting: The first, detailed most extensively in the published papers from the inaugural International Conference on E-Voting (Alkassar and Volkamer n. pag.) concerns user-side security compromises. These security issues range from voting on unsecure or infected personal computers to the transparency of tabulation, difficulties preventing multiple voting, the complexity of performing a vote recount, and issues with correctly identifying the constituent (European Commission n. pag.). During the course of our literature review and empirical analysis of the Estonian voting system, we concluded that the technologies we assessed can only meaningfully advance the identification process.
The literature regarding infrastructure-side weaknesses is sparse, mostly due to the advanced technical knowledge required to meaningfully contribute to these debates. An indispensable text here is the University of Michigan’s security analysis of the Estonian internet voting system in 2013. Because of the privileged back-end access and technical knowledge the researchers possessed, they detailed extensive flaws in the Estonian system, which ranged from flaws in the coding of software packages, server-side attacks, poor operational security by voting personnel, or the involvement of private companies in the electoral process (Durumeric et al. 2).
Privacy issues predominantly (but not exclusively) centered around client-side infrastructure. The primary privacy concern with regards to i-Voting is based on the safety of the identity of the voter, and the secrecy of their vote (NCFER 62). This is a central pillar of democracy, and something that cannot be compromised under any circumstances, as it opens the way to vote-buying, intimidation or political persecution. An important case study here is The Netherlands’ experience with electronic voting. The Netherlands were one of the earliest adopters of voting machines, however on the 16th of May 2008, the government confirmed that all future democratic elections would be held via paper and pencil only. The voting machine employed, the Nedap ES3B, not only raised concerns about the involvement of private companies in the electoral process, but came under heavy criticism for being extremely insecure. This, in turn, led to a group of Dutch computer scientists forming We Do Not Trust Voting Computers and pushing for a ban on the machine after it was discovered it can be hacked and identities extracted in only five minutes (Gonggrijp and Hengeveld n. pag.)
Furthermore, a technique known as Van Eck Phreaking, discovered by Dutch computer researcher Wim van Eck in 1985, was able to compromise the secrecy of votes by the Dutch secret service from up to ten metres away (Gonggrijp and Hengeveld, n.pag.). The technique uses custom hardware to receive side-band electromagnetic signals and convert these signals to recreate the device’s use (van Eck n. pag.).
What Now?
The implementation of biometrics can improve certain security features of i-Voting systems, as well as contribute to a general sentiment of trust. Widely accessible fingerprint readers and face-recognition software provides an opportunity for mass implementation of these technologies to reduce certain instances of authentication and identity fraud during the elections. With incorporation of biometric data as means of identification in many countries worldwide, it has the potential to establish a centralised and adaptive system, and ensure correct identification during the course of elections.
However, it appears clear that biometrics do not address many security issues during the vote-processing stage, which hinders their ability to resolve widespread infrastructural, server-side issues. Biometrics are incapable of addressing fundamental weaknesses “in the architecture of the Internet and of the PC hardware and software that is ubiquitous today” (Jefferson et al. 60). In order to effectively adapt the internet voting system, it is crucial to find resolution for drawbacks in all stages of vote processing. Only then can biometrics help to foster a more secure i-Voting process.
References
Abdullah, Nurul Azma, et al. Preserving Anonymity in E-Voting System Using Voter Non-Repudiation Oriented Scheme. 2017, p. 020017. CrossRef, doi:10.1063/1.5005350.
Adesua, Oluwatosin. ONLINE VOTING SYSTEM WITH BIOMETRIC AUTHENTICATION FOR UI ELECTIONS. 23 Mar. 2015.
Alkassar, Ammar, and Melanie Volkamer, editors. E-Voting and Identity First International Conference, VOTE-ID 2007, Bochum, Germany, October 4-5, 2007, Revised Selected Papers. Springer, 2007.
Alvarez, R.Michael, et al. “The Diffusion of Internet Voting. Usage Patterns of Internet Voting in Estonia between 2005 and 2015.” Government Information Quarterly, vol. 33, no. 3, July 2016, pp. 453–59. ScienceDirect, doi:10.1016/j.giq.2016.06.007.
BBC. “The Most Powerful Images from Catalan Referendum.” BBC News, 1 Oct. 2017. www.bbc.com, http://www.bbc.com/news/world-europe-41460037.
Carter Centre. Expert Study Mission Report: Internet Voting Pilot: Norway’s 2013 Parliamentary Elections. Carter Centre, 2014, https://www.regjeringen.no/globalassets/upload/krd/kampanjer/valgportal/valgobservatorer/2013/rapport_cartersenteret2013.pdf.
Durumeric, Zakir, et al. Security Analysis of the Estonian Internet Voting System. ACM Press, 2014, pp. 703–15. CrossRef, doi:10.1145/2660267.2660315.
European Commission. E-Public, e-Participation and e-Voting in Europe – Prospects and Challenges (Study and Options Brief) – Think Tank. http://www.europarl.europa.eu/thinktank/en/document.html?reference=IPOL-JOIN_ET(2011)471584. Accessed 12 Oct. 2017.
Gonggrijp, Rop, and Willem-Jan Hengeveld. Studying the Nedap/Groenendaal ES3B Voting Computer. http://wijvertrouwenstemcomputersniet.nl/images/c/ce/ES3B_EVT07.pdf. Accessed 22 Oct. 2017.
Halderman, Alex. Eesti Internetivalimiste Süsteemi Turvaanalüüs, 31c3. YouTube, https://www.youtube.com/watch?v=wU-v9HBdeDw&feature=youtu.be. Accessed 25 Oct. 2017.
Heather, James, et al. “Verifying Anonymity in Voting Systems Using CSP.” Formal Aspects of Computing, vol. 26, no. 1, Jan. 2014, pp. 63–98. link-springer-com.proxy.uba.uva.nl:2443, doi:10.1007/s00165-012-0268-x.
Jain, Anil, et al. Biometrics: Personal Identification in Networked Society. Springer Science & Business Media, 1999.
Jefferson, David, et al. “Analyzing Internet Voting Security.” Communications of the ACM, vol. 47, no. 10, 2004, p. 59.
Jones, Bill. A Report on the Feasibility of Internet Voting. California Internet Voting Task Force, 2000, http://www.umic.pt/images/stories/publicacoes1/final_report.pdf.
Kawabe, Y., et al. “Role Interchange for Anonymity and Privacy of Voting.” Journal of Logic and Computation, vol. 20, no. 6, Dec. 2010, pp. 1251–88. CrossRef, doi:10.1093/logcom/exq013.
Natgunanathan, I., et al. “Protection of Privacy in Biometric Data.” IEEE Access, vol. 4, 2016, pp. 880–92. IEEE Xplore, doi:10.1109/ACCESS.2016.2535120.
NCFER. National Commission on Federal Election Reform. NCFER, 2001, https://www.verifiedvoting.org/wp-content/uploads/2012/10/NCFER_2001.pdf.
Oliphant, Roland. “Ukraine Election: Petro Poroshenko Declares Victory in Vote Marred by Violence and Intimidation.” The Telegraph, 25 May 2014. www.telegraph.co.uk, http://www.telegraph.co.uk/news/worldnews/europe/ukraine/10855671/Ukraine-election-Petro-Poroshenko-declares-victory-in-vote-marred-by-violence-and-intimidation.html.
Sharma, Stuti, et al. “Online Voting System Using Biometric Security.” Nternational Journal of Enhanced Research in Management & Computer Applications, vol. 2, no. 5, May 2013, pp. 43–46.
Stroup, Jake. “Biometric Identification and Identity Theft.” The Balance, 5 Oct. 2017, https://www.thebalance.com/biometric-identification-and-identity-theft-1947595.
Stroup, Jake. “Use High-Tech Personal Security To Keep Your Information Safe.” The Balance, 29 June 2016, https://www.thebalance.com/biometric-identification-and-identity-theft-1947595.
van Eck, Wim. Electromagnetic Radiation from Video Display Units: An Eavesdropping Risk? 1985, http://www.tscm.com/vaneck85.pdf.