Cloud computing: Shadow, the line between privacy and illegality
With the introduction of streaming services such as Netflix, Hulu or Disney+ a new era of cloud computing emerged. After the already existing cloud storage services, for example GoogleDrive, you now too can stream your favorite films through the use of an extern computer system, without having installed any software or hardware yourself.
Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction (Mell and Grance 2009)
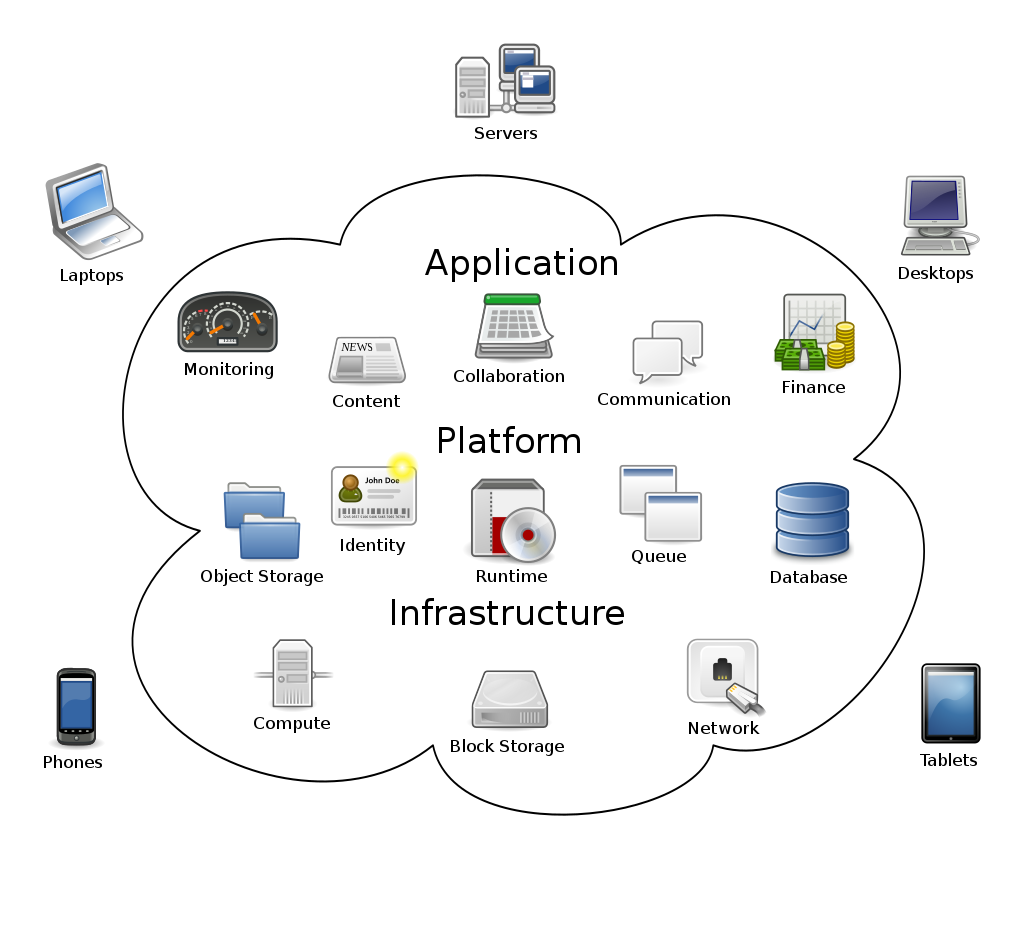
But not only films can be streamed, the newest cloud computing technology does now also stream games. In an article on the website TechCrunch they explained that Cloud gaming is the newest trend where the user does not need to download and install a game with too high demands for their computer, but can outsource this to a remote server where the games are rendered and streamed to the users their screens over the internet (Matney 2019).
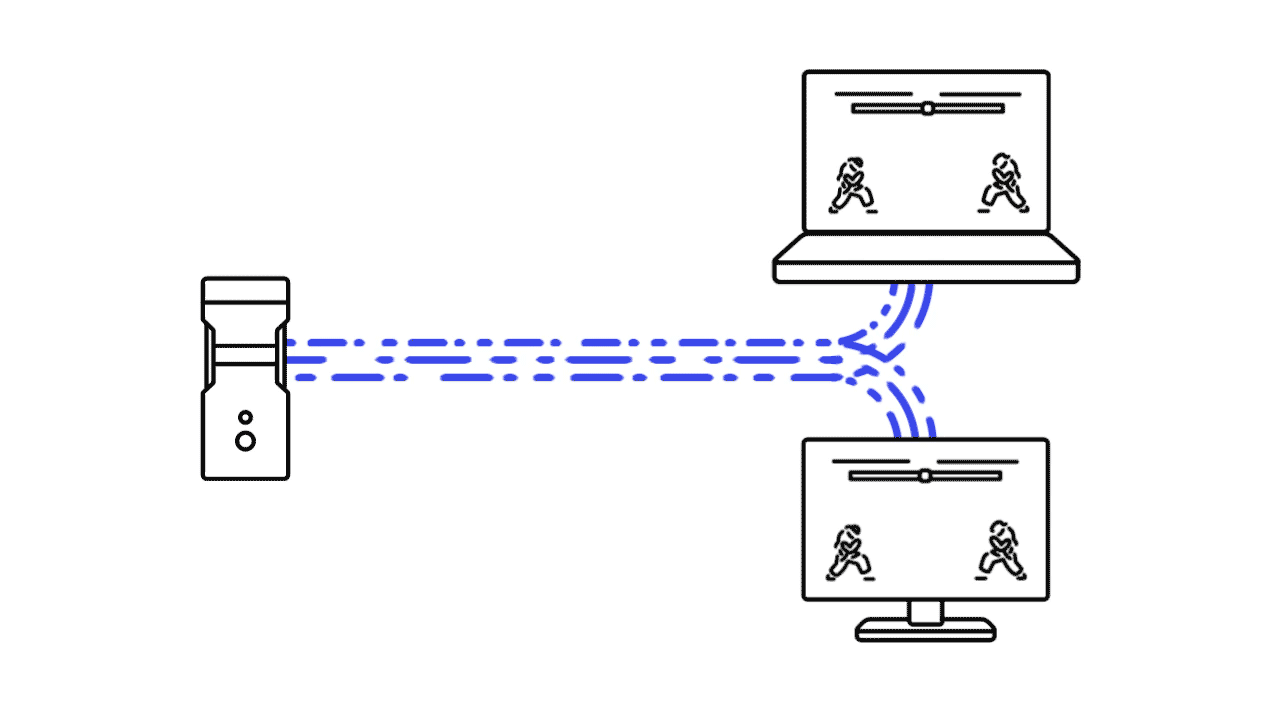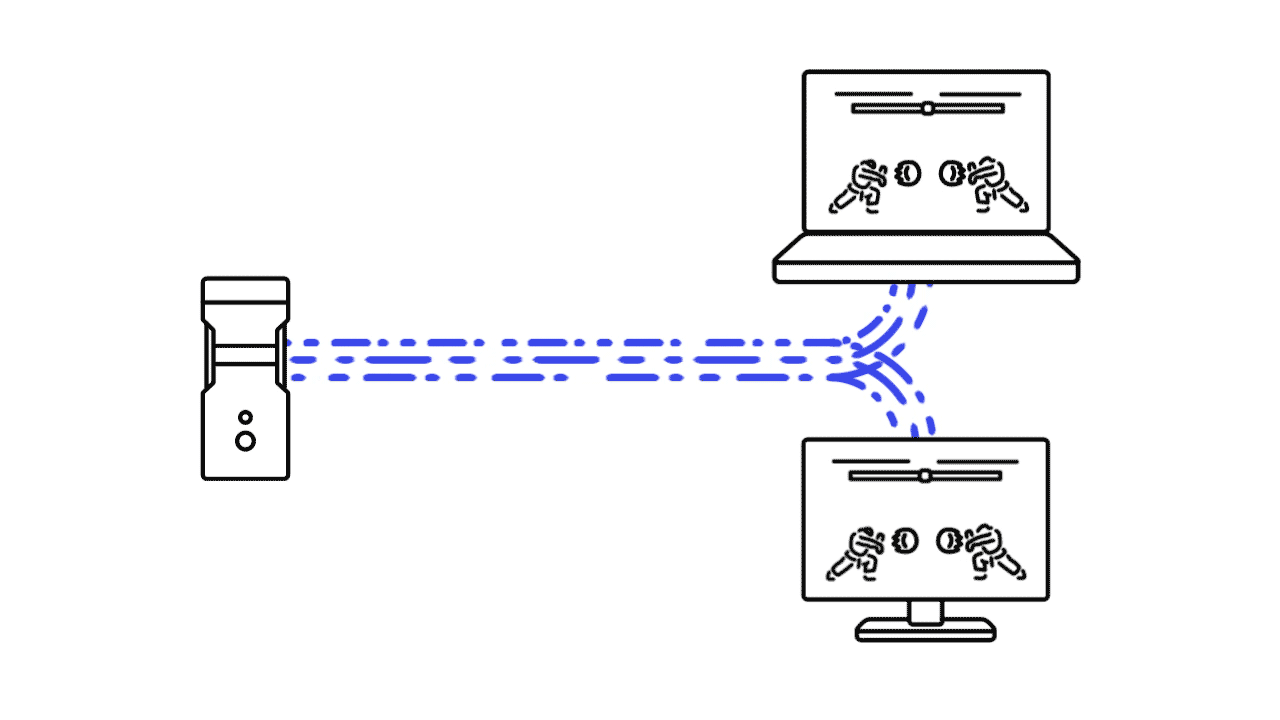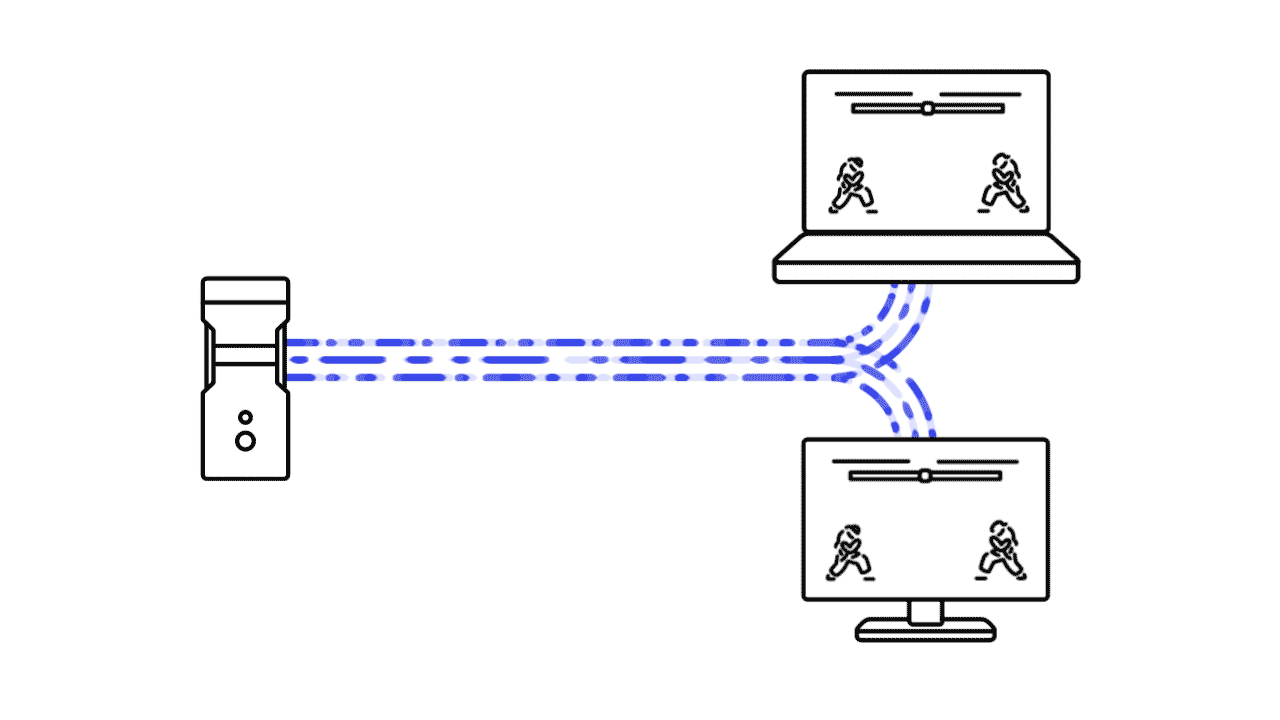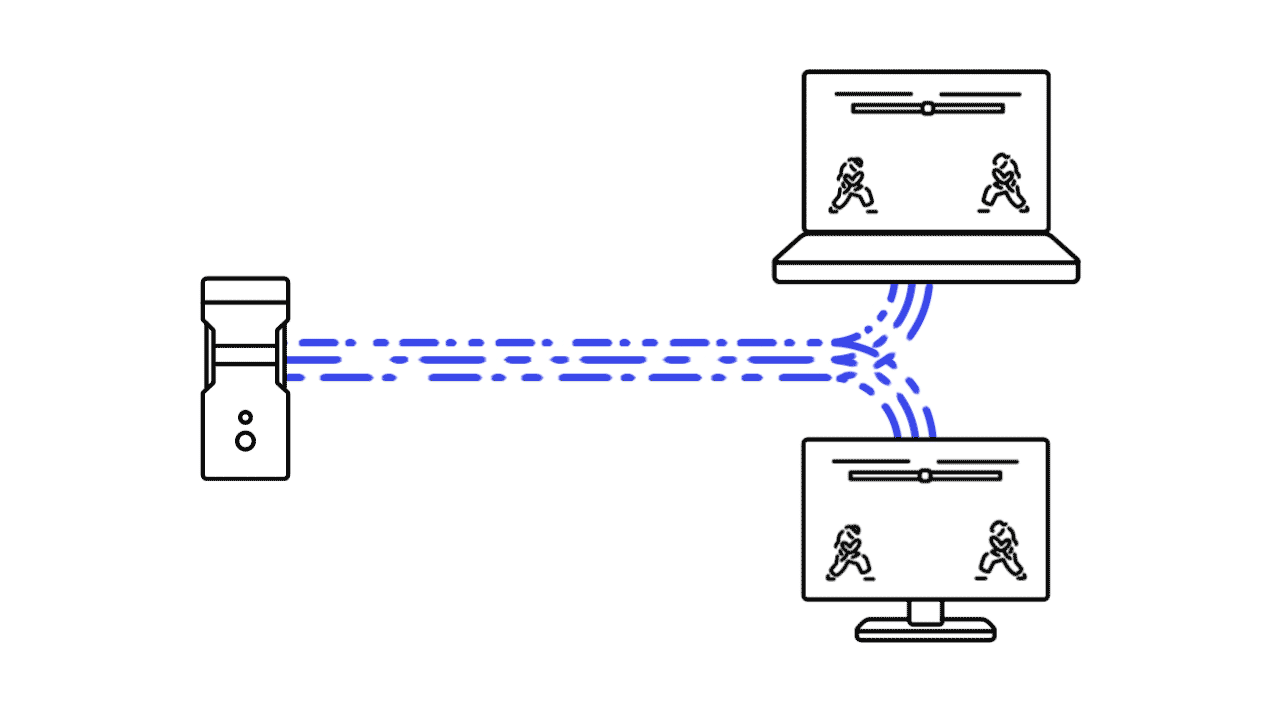
Shadow is a cloudgaming subscription based service that offers this experience but way more. Not only does it takes care of the streaming of games, to do this it creates a whole new cloud computer (a windows 10 environment) for you where you can download, install and play your games on. It’s your own high end computer rendered through another computer.
But with new technologies come new issues. On this rendered cloud computer you can store your own personal data. You can do everything you can do on your own private computer but… is this also private? With Shadow you can still illegally download the games you want to play or any other content for that matter. You can still perform illegal activities like you could on your own regular computer, you just do them on a different server. Ofcours the law should be uphold concerning illegal activity and should be amerced when necessary to counter it. Than again, this should mean your data can be looked at when necessary. Which in turn means the possibility exist they can always look at your personal data. The lingering question now is: should your privacy be diminished for countering illegal activity.
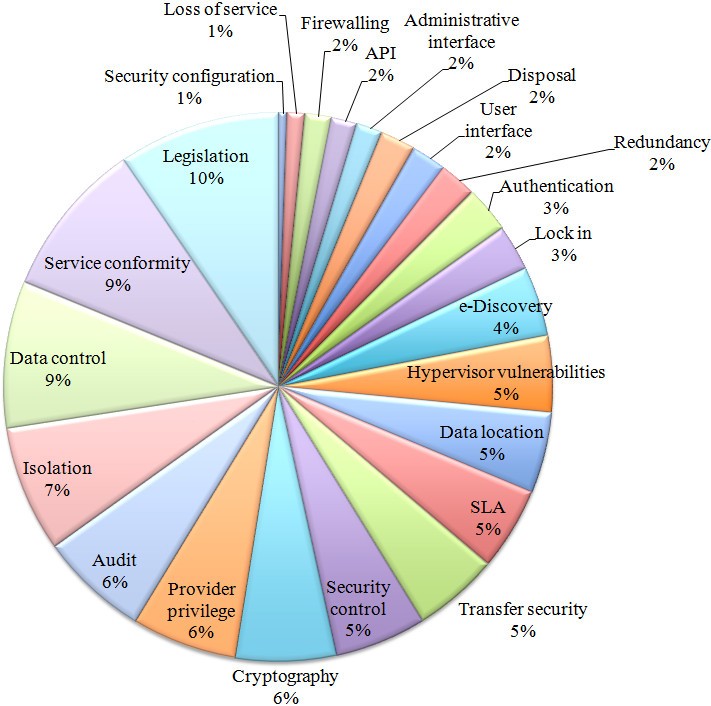
Gonzalez et al. (2012) did a full review on the main security problems regarding cloud computing. The three major problems identified are legal issues, compliance and loss of control over data. This pie diagram shows there are a lot of concerns about the security of cloud computing.
The National Institute of Standards and Technology (NIST), a brand of the US Department of Commerce also acknowledge the security challenges cloud computing presents and has therefore published Guidelines on Security and Privacy in Public Cloud Computing (Grance and Jansen 2011). You can acces them here: https://www.nist.gov/publications/guidelines-security-and-privacy-public-cloud-computing.
Jaeger, Lin and Grimes (2008) say that to protects the privacy of cloud users, care must be taken to guard both users their data and applications for manipulating that data. They state that it appears that users are willing to accept certain monitoring based on forms of automated learning of users their activities and content in exchange for increased convenience, storage capacity, and searching ability and that maybe the same will be for cloud computing. They suggest one obvious solution, for the user to encrypt whatever data resides in the cloud, although this is mainly for the storage of data.
Personally I think we indeed accept a little monitoring for increased convenience, especially when talking about monitoring online activity. Regarding our stored personal data the aforementioned encryption could be used. When tackling this problem I think our data should not be made completely invisible. You can already use certain methods to protect your data from being followed such as a VPN. The possibility to tackle illicit activities should still be available. It’s also your own choice to use certain cloud computing services and therefore you know what the consequences can be.
Gonzalez, N., Miers, C., Redígolo, F. et al. 2012. “A quantitative analysis of current security concerns and solutions for cloud computing.” Journal of Cloud Computing: Advances, Systems and Applications 1(11). https://doi-org.proxy.uba.uva.nl:2443/10.1186
Grance, T. and Jansen W. 2011. “Guidelines on Security and Privacy in Public Cloud Computing.” Journal of E-Governance 34:149-151. DOI 10.3233/GOV-2011-0271
Jaeger, P.T., Lin, J. and Grimes, J.M. 2008. “Cloud Computing and Information Policy: Computing in a Policy Cloud?” Journal of Information Technology & Politics 5(3):269-283. https://doi.org/10.1080/19331680802425479
Matney, Lucas 2019. “Cloudgaming is the future of game monetization, not gameplay.” TechCrunch, 29 december. https://techcrunch.com/2019/12/29/cloud-gaming-is-the-future-of-game-monetization-not-gameplay/
P. Mell and T. Grance. 2009. “Draft nist working definition of cloud computing” NIST 15(21).